
NetworkMiner
NetworkMiner is an open source network forensics tool that extracts artifacts, such as files, images, emails and passwords, from captured network traffic in PCAP files. NetworkMiner can also be used to capture live network traffic by sniffing a network interface. Detailed information about each IP address in the analyzed network traffic is aggregated to a network host inventory, which can be used for passive asset discovery as well as to get an overview of which devices that are communicating. NetworkMiner is primarily designed to run in Windows, but can also be used in Linux.
NetworkMiner has, since the first release in 2007, become a popular tool among incident response teams as well as law enforcement. NetworkMiner is today used by companies and organizations all over the world.
Next live online network forensics training: February 23-26, 2026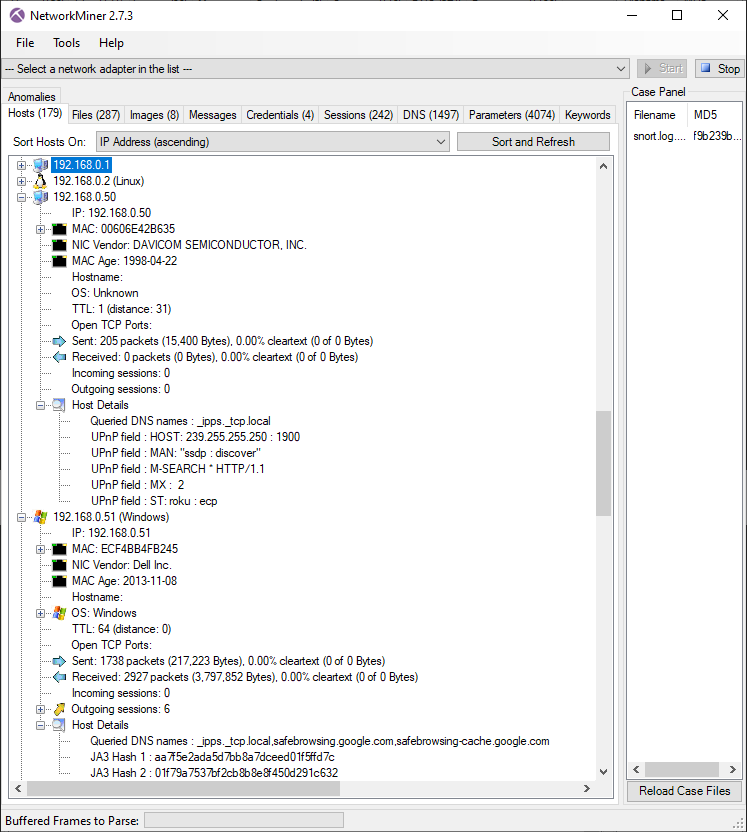
Host inventory in NetworkMiner
|
NetworkMiner Free Edition |
NetworkMiner Professional |
|
|---|---|---|
| Live sniffing | ✅ | ✅ |
| Parse PCAP files | ✅ | ✅ |
| Parse PcapNG files | ✅ | |
| Parse ETL files | ✅ | ✅ |
| Network Packet Carver | ✅ | |
| IPv6 support | ✅ | ✅ |
| Extract files from FTP, TFTP, HTTP, HTTP/2, SMB, SMB2, SMTP, POP3, IMAP and LPR traffic | ✅ | ✅ |
| Extract X.509 certificates from SSL encrypted traffic like HTTPS, SMTPS, IMAPS, POP3S, FTPS etc. | ✅ | ✅ |
| Decapsulation of GRE, 802.1Q, PPPoE, VXLAN, OpenFlow, SOCKS, MPLS, EoMPLS and ERSPAN | ✅ | ✅ |
| Receive Pcap-over-IP | ✅ | ✅ |
| Runs in Windows and Linux | ✅ | ✅ |
| OS Fingerprinting (*) | ✅ | ✅ |
| JA3, JA3S and JA4 extraction | ✅ | ✅ |
| Audio extraction and playback of VoIP calls | ✅ | |
| VoIP audio extraction from RTP without SIP | ✅ | |
| OSINT lookups of file hashes, IP addresses, domain names and URLs | ✅ | |
|
Port Independent Protocol Identification (PIPI) (**) |
✅ | |
| User Defined Port-to-Protocol Mappings (decode as) | ✅ | |
| Export to CSV / Excel / XML / CASE / JSON-LD | ✅ | |
| Configurable file output directory | ✅ | |
| Configurable time zone (UTC, local or custom) | ✅ | |
| Offline IP-to-Country lookup | ✅ | |
| Offline IP ASN lookup | ✅ | |
| DNS Whitelisting (***) | ✅ | |
| Advanced OS fingerprinting | ✅ | |
| Web browser tracing (video tutorial) | ✅ | |
| CIDR filter | ✅ | |
| Advertisement and tracker detection | ✅ | |
| Host coloring support | ✅ | |
| Command line scripting support | ✅ Corporate License required | |
| Price | Free | $ 1300 USD |
|
Download NetworkMiner |
Buy NetworkMiner Professional | |
|
* Fingerprinting of Operating Systems (OS) is performed by using databases from Satori and p0f ** Identified protocols include: DNS, FTP, HTTP, HTTP2, IRC, Meterpreter, NetBIOS NameService, NetBios SessionService, Socks, Spotify's Server Protocol, SSH, SSL, TDS (MS-SQL) and TPKT *** Domain names in the DNS tab are checked against the Alexa top 1,000,000 sites |
||
NetworkMiner can extract files, emails and certificates transferred over the network by parsing a PCAP file or by sniffing traffic directly from the network.
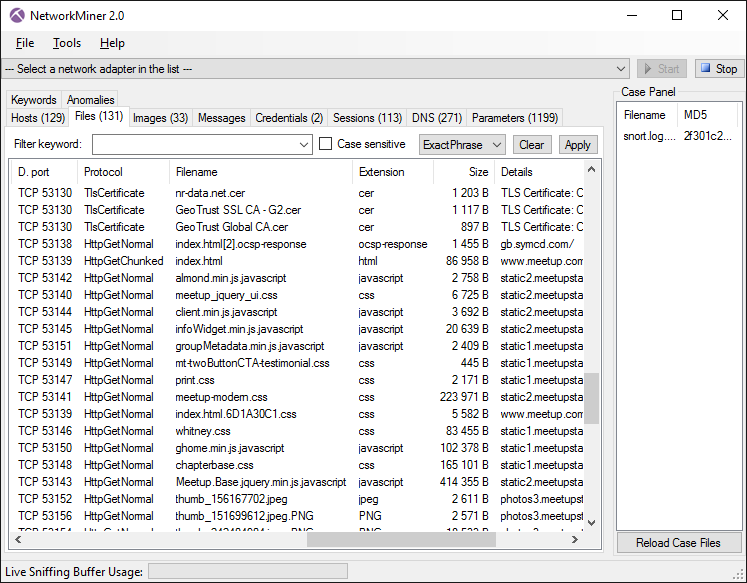
NetworkMiner showing files extracted from sniffed network traffic to disk
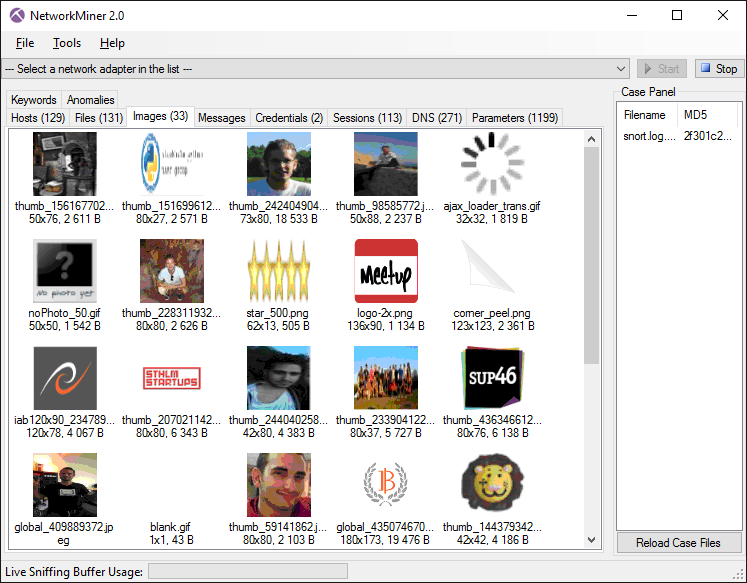
NetworkMiner showing thumbnails for images extracted to disk
User credentials (usernames and passwords) for supported protocols are extracted by NetworkMiner and displayed under the "Credentials" tab. The credentials tab sometimes also shows information that can be used to identify a particular person, such as user accounts for internal or online services.

Another very useful feature is that the user can search sniffed or stored data for keywords. NetworkMiner allows the user to insert arbitrary string or byte-patterns that shall be searched for with the keyword search functionality.
NetworkMiner Professional can be delivered either as an Electronic Software Download (ESD) or shipped physically on a USB flash drive. The product is exactly the same, regardless of delivery method. NetworkMiner is a portable application that doesn't require any installation, which means that the USB version can be run directly from the USB flash drive. However, we recommend that you copy NetworkMiner to the local hard drive of your computer in order to achieve maximum performance.
» How To Buy NetworkMiner Professional «
Download NetworkMiner
The latest version of NetworkMiner can be downloaded from:
» https://www.netresec.com/?download=NetworkMiner « (executable application)
SHA256 hash: 782e3d4d0b917a5aadf59966ab7d21ab30dbd593eff14e426f2b580a2e3f89e1 (hash link)
» https://www.netresec.com/?page=NetworkMinerSourceCode « (source code)
Fixed-version download link for NetworkMiner 3.1:
» https://download.netresec.com/networkminer/NetworkMiner_3-1.zip" «
Windows Pro and Enterprise users, who wish to analyze malicious network traffic in Windows while minimizing the risk of infecting themselves, can download a Windows Sandbox version of NetworkMiner from here:
» https://www.netresec.com/?download=NetworkMinerSandbox « (learn more)
Change Log
NetworkMiner Videos




Additional instruction videos for NetworkMiner can be found on our video tutorial page.
FAQ – Frequently Asked Questions
Q: How do I run NetworkMiner in Linux?
Install Mono (cross platform, open source .NET framework), download and extract NetworkMiner and then start NetworkMiner with mono NetworkMiner.exe. For more details, please see our How To install NetworkMiner in Linux blog post.
Q: Can I run NetworkMiner on a Mac?
The support for Mono on macOS is very limited, but you can try the following solution:
Install Mono with "
Q: How do I sniff network traffic with NetworkMiner in Windows?
To sniff with raw sockets you'll first need to create a firewall rule to allow NetworkMiner to capture incoming TCP packets. Run the command "wf.msc" to start Windows Defender Firewall and create a new inbound rule for NetworkMiner.exe. Next, start NetworkMiner as administrator and select a network interface in the drop down list at the top of the GUI. Finally, start a live packet capture by clicking the Start button.
Q: Can NetworkMiner sniff network traffic in Linux?
NetworkMiner only supports live sniffing through PCAP-over-IP when Mono is used.
Q: Can NetworkMiner extract files from HTTPS traffic?
NetworkMiner is not designed to perform decryption, so files transferred inside TLS encrypted sessions, like HTTPS, will not be extracted. X.509 certificates from TLS handshakes will be extracted to disk by NetworkMiner though. You can use a TLS proxy, like PolarProxy, in order to decrypt TLS traffic and forward decrypted traffic to NetworkMiner. See our video PolarProxy in Windows Sandbox for more details.
Q: Is the extracted data stored locally or in the cloud?
NetworkMiner only stores data locally on the end-user device.
Q: I'm unable to start NetworkMiner. I get an error message saying "Could not load type 'System.ValueTuple`2' from assembly 'mscorlib, Version=4.0.0.0, Culture=neutral, PublicKeyToken=b77a5c561934e089'". How can this be fixed?
Please install .NET framework 4.8 or later.
Q: Is it safe to open PCAP files containing malicious traffic with NetworkMiner in Windows?
No. NetworkMiner automatically extracts transferred files from opened PCAP files, including files potentially containing malware. Accidentally opening an extracted malicious file might lead to self-infection. Recommended practices are to either run NetworkMiner in Linux or in a Windows Sandbox to minimize the risk of self-infection. NetworkMiner Professional can also defang executable files to avoid accidental self-infection.
More Information
There are also several blog posts about NetworkMiner on the NETRESEC Network Security Blog:
- NetworkMiner 2.0 Released
- Pcap-over-IP in NetworkMiner
- Network Forensic Analysis of SSL MITM Attacks
- Command-line Network Forensics with NetworkMinerCLI
- NetworkMiner Video Tutorials on the Intertubes
- Webmail Information Leakage
- Analyzing the TCP/IP Weapons School Sample Lab
⛏
