NetworkMiner 1.6 Released
We've released version 1.6 of NetworkMiner today!
 Image credits: Confetti in Toronto by Winnie Surya
Image credits: Confetti in Toronto by Winnie Surya
The new features in NetworkMiner 1.6 include:
- Drag-and-Drop
Reassembled files and images can be opened with external tools by drag-and-dropping items from NetworkMiner's Files or Images tabs onto your favorite editor or viewer. - Email extraction
Improved extraction of emails and attachments sent over SMTP. - DNS analysis
Failed DNS lookups that result in NXDOMAIN and SERVFAIL are displayed in the DNS tab along with the flags in the DNS response. - Live sniffing
Improved live sniffing performance. - PCAP-over-IP
Remote live sniffing enabled by bringing the PCAP-over-IP feature into the free open source version of NetworkMiner.
Identifying Malware DNS lookups
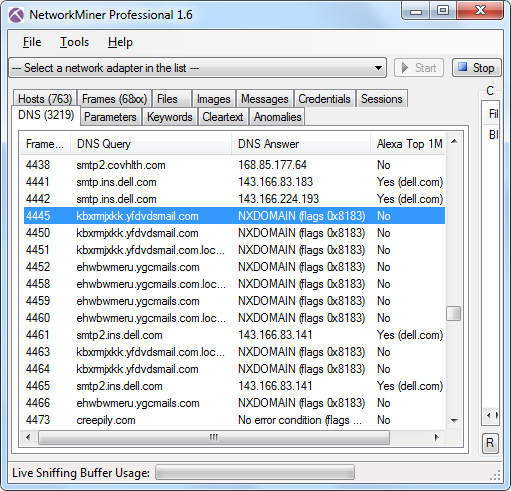
DNS traffic from the Kuluoz-Asprox botnet (PCAP file available via Contagio)
Note the NXDOMAIN responses and “No” in Alexa top 1 million column in the screenshot above; these domains are probably generated by a domain generation algorithm (DGA).
Live Sniffing with Pcap-over-IP
The PCAP-over-IP functionality enables live sniffing also on non-Windows machines, simply by running tcpdump (or dumpcap) and netcat like this:
# tcpdump -i eth0 -s0 -U -w - | nc localhost 57012
To receive the Pcap-over-IP stream in NetworkMiner, simply press Ctrl+R and select a TCP port.
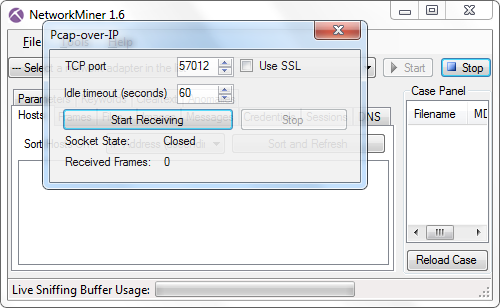
For more information about this feature please see our previous blog post about the PCAP‑over‑IP feature.
NetworkMiner Professional
The professional version of NetworkMiner additionally contains the following improvements of the command line tool NetworkMinerCLI:
- Enabled reading of PCAP and PcapNG data from standard input (STDIN)
- Full support for PCAP-over-IP
- More detailed DNS logging in NetworkMinerCLI's CSV export of DNS responses
The ability to read PCAP data from STDIN with NetworkMinerCLI makes it really simple to do live extraction of emails and email attachments. Here's an example showing how to do live SMTP extraction in Linux:
# tcpdump -i eth0 -s0 -w - port 25 or 587 | mono NetworkMinerCLI.exe -r - -w /var/log/smtp_extraction/
The syntax for extracting emails and attachments in Windows is very similar:
C:\>dumpcap.exe -i 1 -f "port 25 or 587" -w - | NetworkMinerCLI.exe -r -
The TCP ports 25 and 587, which are used in the capture filter above, are the standard port numbers for SMTP. In order to do live extraction of files sent over HTTP, simply use “port 80” as capture filter instead. Likewise, X.509 certificates can also be extracted from HTTPS sessions simply by using “port 443” as capture filter.
Download NetworkMiner 1.6
The most recent release of the free (open source) version of NetworkMiner can be downloaded from SourceForge or our NetworkMiner product page. Paying customers can download an update for NetworkMiner Professional from our customer portal.
Credits
We would like to thank Dan Eriksson (FM CERT) and Lenny Hansson (Danish GovCERT) for submitting bug reports and feature requests.
Posted by Erik Hjelmvik on Monday, 16 June 2014 11:00:00 (UTC/GMT)
Tags: #Netresec #NetworkMiner #Professional #SMTP #Extract #DNS #PCAP-over-IP



