TorPCAP - Tor Network Forensics

Unencrypted network traffic, destined for the Tor network, is sent between localhost TCP sockets on computers running Tor clients, such as the Tor Browser. In this blog post I show how anonymous Tor browsing can be visualized, by loading a PCAP file with localhost traffic into NetworkMiner. We call this technique TorPCAP.
Tor is a secure platform that enables users to browse the web anonymously. The Tor Project website describes the tool as:
“Tor is free software and an open network that helps you defend against traffic analysis”
It is also possible to host anonymous “onion services” on the Dark Web using Tor:
“Tor makes it possible for users to hide their locations while offering various kinds of services, such as web publishing or an instant messaging server. Using Tor "rendezvous points," other Tor users can connect to these onion services, formerly known as hidden services, each without knowing the other's network identity.”
Capturing Tor Traffic Before it gets Encrypted
Tor installations include a SOCKS proxy listening on TCP port 9150 on localhost (127.0.0.1). This local SOCKS proxy is used by the Tor Browser, which connects to the proxy in order to have its traffic encrypted and forwarded to the Tor network. This means that by sniffing traffic on localhost it’s actually possible to create a solid forensic trail of all traffic a PC sends to and from the Tor network.
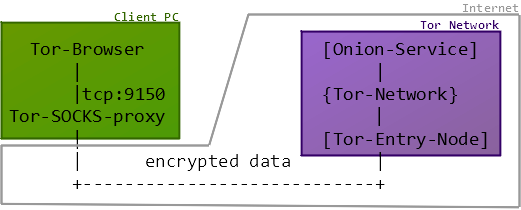
You can use tcpdump to capture the localhost traffic on PCs running the Tails OS or Tor Browser in MacOS or Linux. If you’re running the Tor Browser in Windows, then we recommend using RawCap to sniff the localhost traffic (RawCap is a portable standalone tool that doesn’t need WinPcap or NDIS drivers to work).
In order to make sense of the captured traffic you need a tool that can parse the SOCKS protocol (RFC 1928). NetworkMiner includes a SOCKS parser since version 2.1, which can be used to extract and reassemble data going to and from the Tor network.

Demo: Analysing TorPCAP Network Traffic
A user, let’s call him “Eldon”, used Tor for some dark-web activity on November 30, 2018. Eldon was using the Tor Browser on a Windows PC and RawCap was used to capture the localhost network traffic from Eldon’s computer. A PCAP file with the captured packets from Eldon’s PC can be accessed here. Please feel free to open this capture file with NetworkMiner, in order to follow along in this analysis.
File : rawcap-localhost-tor.pcap
Size : 1.47 MB
SHA256 : 9134FA542B388498C2A58A2E1424FCD4AF466CE7117DBE9AAFD0A031CC8209B8
The “Files” tab in NetworkMiner contains a list of all files that have been reassembled from the analyzed PCAP file. This file listing reveals that Eldon used the “not Evil” search engine (hss3uro2hsxfogfq[.]onion) to search for “buy fake passports” in frame 1136.
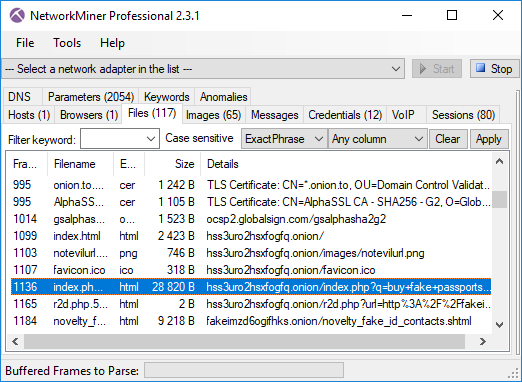
The search result page from not Evil has been reassemled by NetworkMiner as “index.php.CB66877E.html”. By opening this HTML document in a browser we can see which search results Eldon got (no Internet connection is needed to open the reassembled html).
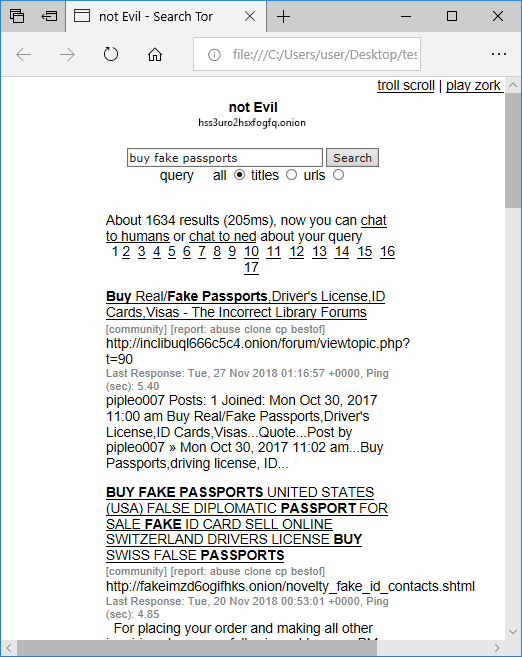
The “Browsers” tab in NetworkMiner Professional shows that Eldon followed the link for entry #2 in his search results (BUY FAKE PASSPORTS [...]), leading him to the “fakeimz[...].onion” website.
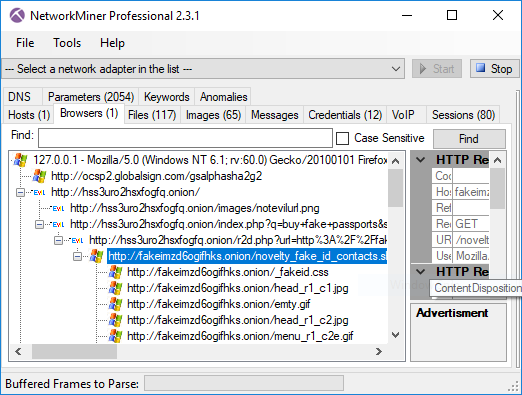
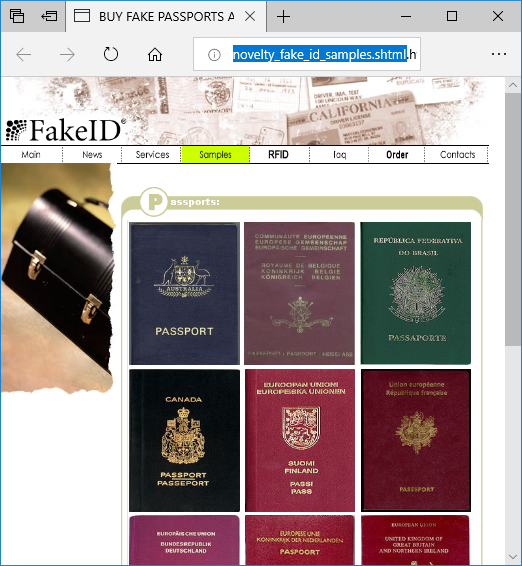
Eldon then proceeded to list the available passports (see the reassembled file “novelty_fake_id_samples.shtml” in frame 1837) and chose the UK passport (“pp-uk-open-big.jpg”).
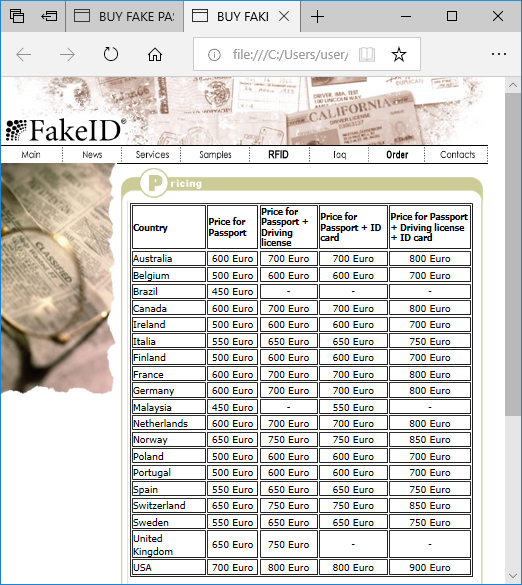
As Eldon proceeded he got a price list for the fake passports offered at this site (“novelty_fake_id_pricing.shtml”), but we don’t see any evidence of him actually completing a purchase of a fake UK passport.
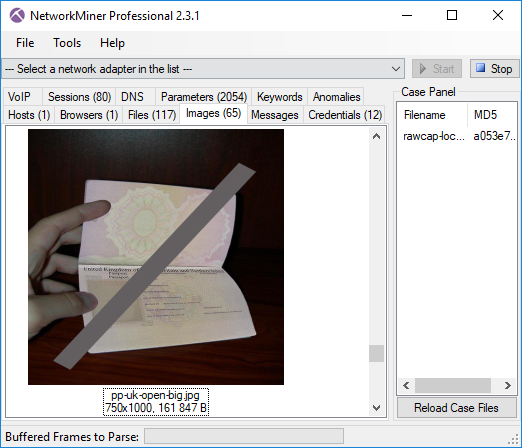
If we go back to the Images tab in NetworkMiner, and scroll a bit further down we see a picture of a gun. Let’s see where it comes from.
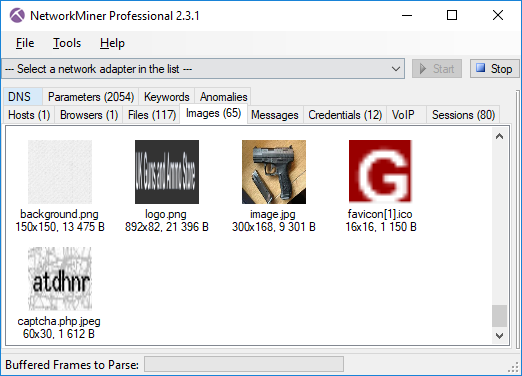
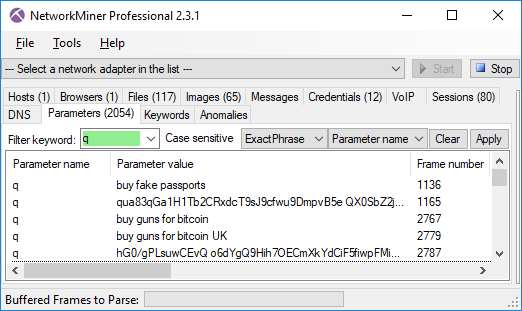
It turns out Eldon also searched for “buy guns for bitcoin UK”. You can list all search engine queries by looking for entries in the “Parameters” tab with parameter name “q”. This technique is applicable for the “not Evil” search engine as well as most clearnet search engines, like Google, Bing, Yahoo! and DuckDuckGo (disregarding the fact that they use TLS).
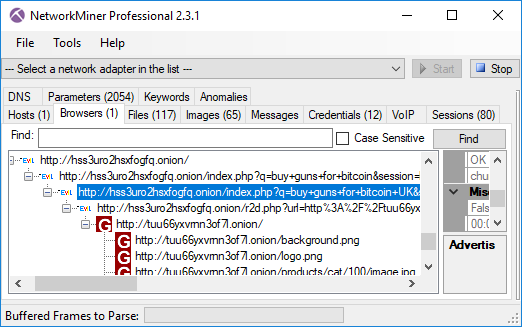
The Browsers tab shows us that Eldon clicked on a link to the “UK Guns and Ammo Store” (tuu66[...].onion).
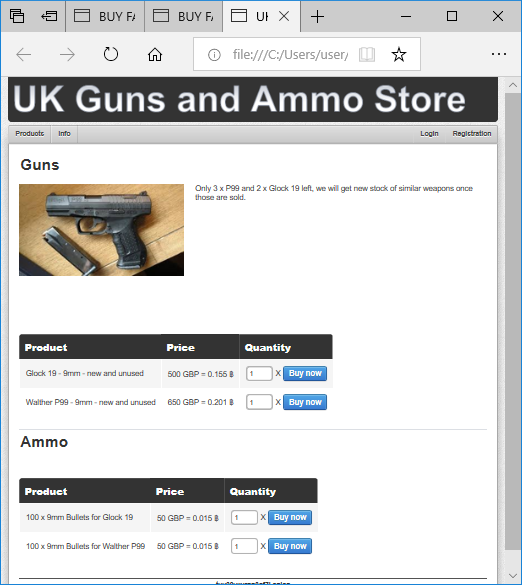
This website has also been passively reassembled by NetworkMiner and can be opened offline in a browser (see “index[2].html”).
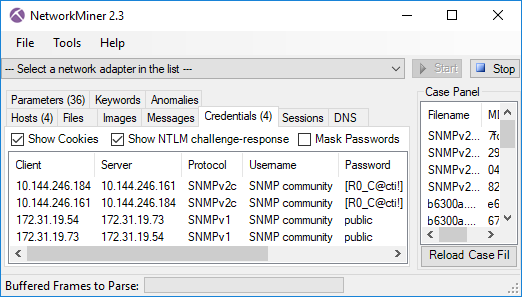
The Credentials tab in NetworkMiner shows the username and password used by Eldon to log into the website:
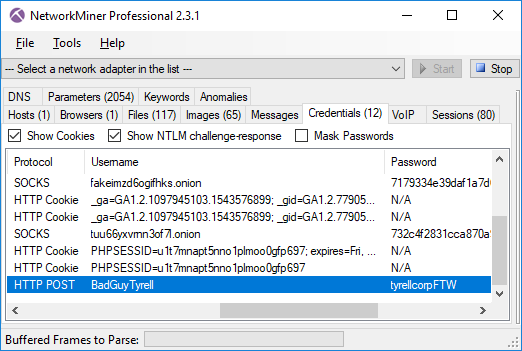
After logging in, Eldon puts two items in his shopping cart (see “cart.php[1].html”), but gets a message saying “Not enough balance for this order” when clicking the “Continue to Checkout” link. It seems Eldon’s account at the dark-web weapons store doesn’t have any Bitcoins (see “wallet.php.html”)
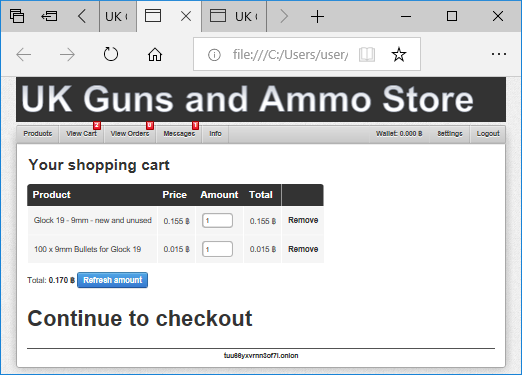
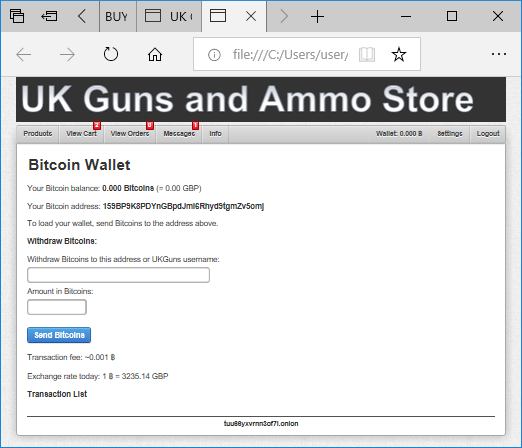
Side Note - Web Trackers and Tor
It is considered bad practice to use clear-net tracking services, like Google Analytics, to track users visiting an onion service. However, we noticed that the fake passports website uses a Google Analytics script with tracking ID “UA-19359933-1”.
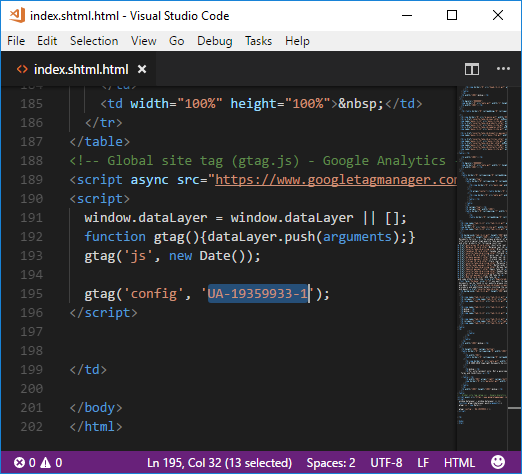
Googling this ID led us to this very similar website:
hxxp://www.buypassportsfake[.]cc
![hxxp://www.buypassportsfake[.]cc](https://www.netresec.com/images/BuyPassportsFake-cc_522x464.png)
Posted by Leon Kowalski on Wednesday, 12 December 2018 09:33:00 (UTC/GMT)
Tags: #Tor #PCAP #NetworkMiner #RawCap #SOCKS #127.0.0.1







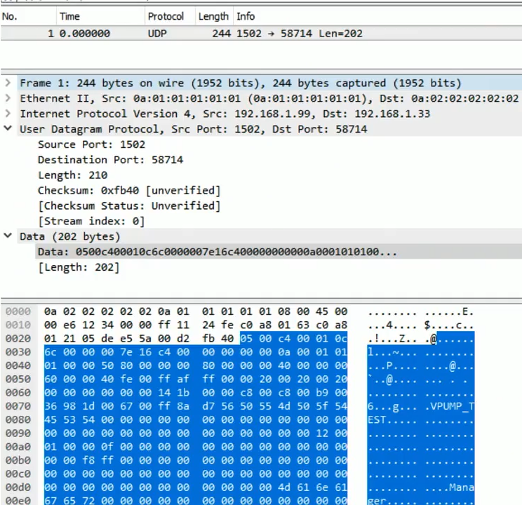

 Image: NetworkMiner Professional 2.3.2 with “vm_win7.pcap” from University of Twente’s
Image: NetworkMiner Professional 2.3.2 with “vm_win7.pcap” from University of Twente’s