Detecting the Pony Trojan with RegEx using CapLoader
This short video demonstrates how you can search through PCAP files with regular expressions (regex) using CapLoader and how this can be leveraged in order to improve IDS signatures.
The EmergingThreats snort/suricata rule mentioned in the video is SID 2014411 “ET TROJAN Fareit/Pony Downloader Checkin 2”.
The header accept-encoding header with quality factor 0 used by the Pony malware is:
Accept-Encoding: identity, *;q=0
And here is the regular expression used to search for that exact header: \r\nAccept-Encoding: identity, \*;q=0\r\n
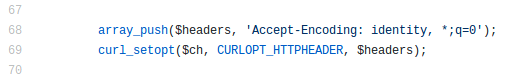
After recording the video I noticed that the leaked source code for Pony 2.0 actually contains this accept-encoding header as a
hard-coded string. Have a look in the
redirect.php file, where they set
curl’s
Wanna learn more about the intended use of quality factors in HTTP accept headers?
Then have a look at section 14.1 of RFC 2616section 5.3.4 of RFC 7231, which defines how to use qvalues (i.e. quality factors) in the Accept-Encoding header.
Finally, I'd like to thank Brad Duncan for running the malware-traffic-analysis.net website, your PCAP files often come in handy!
Update 2018-07-05
I submitted a snort/suricata signature to the Emerging-Sigs mailinglist after publishing this blog post, which resulted in the Emerging Threats signature 2014411 being updated on that same day to include:
content:"|0d 0a|Accept-Encoding|3a 20|identity,|20 2a 3b|q=0|0d 0a|"; http_header;Thank you @EmergingThreats for the fast turnaround!
Posted by Erik Hjelmvik on Wednesday, 04 July 2018 07:39:00 (UTC/GMT)
Tags: #video #regex #malware #IDS #curl #malware-traffic-analysis.net #videotutorial



