CapLoader 1.7 Released
We are happy to announce the release of
CapLoader 1.7!

Here’s an overview of what’s new in this release:
- Regular expression searching
- Lookup of IP addresses using online services
- Lookup of domain names using online services
- Improved protocol fingerprinting speed and precision
- Support for GRE, IGMP and ICMPv6 flows
- More precise period estimation of “periodic services”
Regular Expressions Search
CapLoader’s “Find Keyword” window has been extended with an option to search flows using regular expressions (regex) as an alternative to searching for strings or byte sequences. With help of the powerful regex syntax built into .NET this new search option enables very flexible searching.
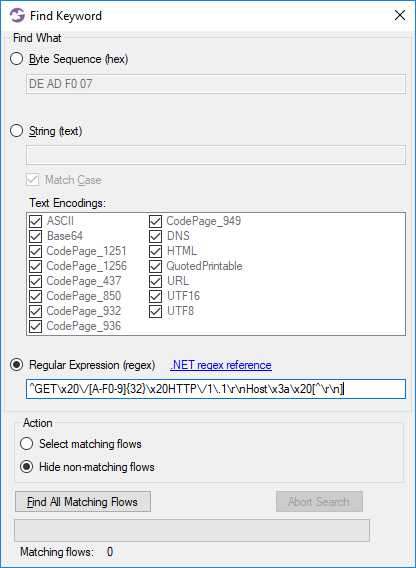
Image: Searching for Alfa Ransomware flows using regex
The Find Keyword window can be opened by clicking Edit > Find Keyword, or by pressing
You can learn more about regex searching with CapLoader in our short video called "Detecting the Pony Trojan with RegEx using CapLoader".
OSINT Lookups of IP Addresses and Domains
We added support for querying online services for IPs and domain names to the latest release of NetworkMiner, now it’s time to add this very handy feature to CapLoader as well.
Right-clicking a Flow, Service or Host in CapLoader brings up a context menu with links to various online resources that might have more details regarding the clicked IP address or domain name.
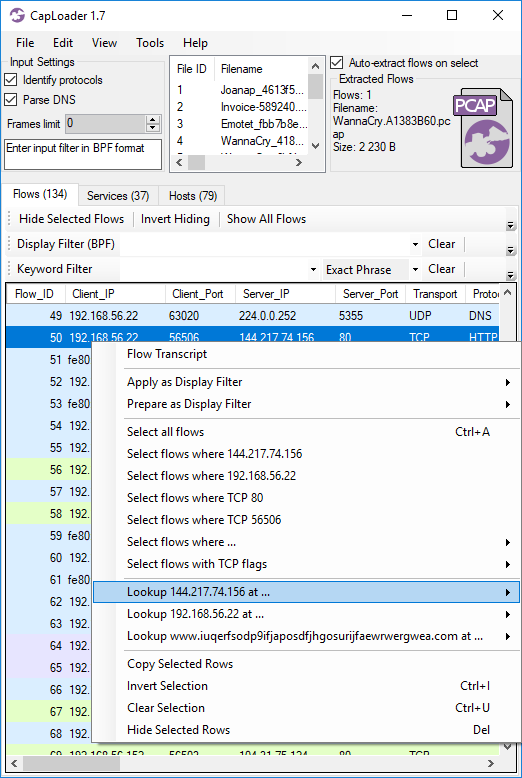
The services available for IP address OSINT lookup include:
APNIC Whois, Censys, Cymon, ExoneraTor, Google Public DNS, GreenSnow.co, Hurricane Electric, IBM X-Force, Internet Storm Center, mnemonic Passive DNS, PacketTotal, SecurityTrails, Shodan, ThreatCrowd, ThreatMiner, UrlQuery and VirusTotal.
The domain name lookup menu contains a similar set of providers:
Cymon, Google Public DNS, Google Safe Browsing, Hybrid Analysis, IBM X-Force Exchange, mnemonic Passive DNS, MXToolBox, MyWOT, Norton Safe Web, PacketTotal, SecurityTrails, ThreatCrowd, ThreatMiner, URL Void, UrlQuery, VirusTotal, Website Informer, Webutation and Whoisology.
Protocol Identification
The dynamic protocol detection (or Port Independent Protocol Detection, aka “PIPI”) in CapLoader has been improved to support even more protocols than before. We have also fine-tuned the protocol identification algorithm to be both faster and more accurate.
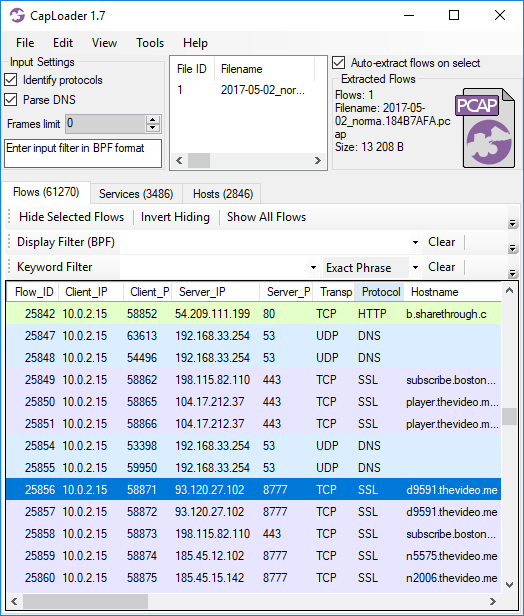
Image: Traffic to TCP 8777 identified as SSL (PCAP file from Stratosphere IPS)
Updating to the Latest Release
Users who have previously purchased a license for CapLoader can download a free update to version 1.7 from our customer portal. All others can download a free 30 day trial from the CapLoader product page (no registration required).
Credits
We’d like to thank Michael Nilsson for suggesting the IP and domain name lookup feature and Tohar Braun for suggesting RegEx search support. We’d also like to thank Ralf Alvarsson and Jarmo Lahtiranta for reporting bugs that have been resolved in this release.
Posted by Erik Hjelmvik on Tuesday, 03 July 2018 11:37:00 (UTC/GMT)
Tags: #CapLoader #regex #keyword #pcap #GRE #OSINT #IP