Walkthrough of DFIR Madness PCAP
I recently came across a fantastic digital forensics dataset at dfirmadness.com, which was created by James Smith. There is a case called The Stolen Szechuan Sauce on this website that includes forensic artifacts like disk images, memory dumps and a PCAP file (well, pcap-ng actually). In this video I demonstrate how I analyzed the capture file case001.pcap from this case.
Follow Along in the Analysis
Please feel free to follow along in the analysis performed in the video. You should be able to use the free trial version of CapLoader and the free open source version of NetworkMiner to perform most of the tasks I did in the video.
Here are some of the BPF and Column Criteria filters that I used in the video, so that you can copy/paste them into CapLoader.
- net 10.0.0.0/8
- Umbrella_Domain =
- not ip6 and not net 224.0.0.0/4
- host 194.61.24.102 or host 203.78.103.109 or port 3389
References and Links
- Original writeup and capture file by James Smith
- CapLoader
- NetworkMiner
- Alexa top sites
- Cisco Umbrella 1 Million domain list
- Understanding user-agent strings
- Operating System Version
- Python SimpleHTTP web server
- coreupdater.exe on VirusTotal
Timeline
All events in this timeline take place on September 19, 2020. Timestamps are in UTC.
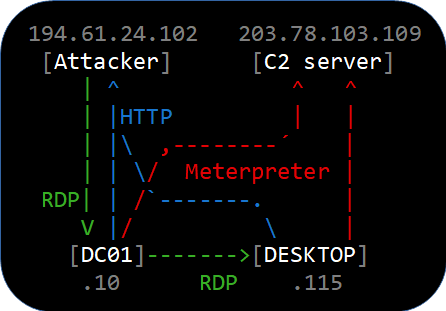
- 02:19:26 194.61.24.102 performs RDP brute force password attack against DC01.
- 02:21:47 RDP password brute force successful.
- 02:22:08 194.61.24.102 connects to DC01's RDP service as Administrator.
Duration: 9 sec. - 02:22:36 194.61.24.102 connects to DC01's RDP service as Administrator again.
Duration: 30 min. - 02:24:06 DC01 downloads coreupdater.exe from 194.61.24.102 using IE11.
- 02:25:18 DC01 establishes Metrepreter reverse_tcp connection to 203.78.103.109.
Duration: 4 min. - 02:29:49 DC01 re-establishes Metrepreter reverse_tcp connection to 203.78.103.109.
Duration: 23 min. - 02:35:55 DC01 connects to DESKTOP's RDP service Administrator (username in Kerberos traffic).
Duration 16 min. - 02:39:58 DESKTOP download coreupdater.exe from 194.61.24.102 using MS Edge.
- 02:40:49 DESKTOP establishes Metrepreter reverse_tcp connection to 203.78.103.109.
Duration: 2h 58 min. - 02:56:03 194.61.24.102 connects to DC01's RDP service as Administrator one last time.
Duration: 1 min 38 sec. - 02:56:38 DC01 re-establishes Metrepreter reverse_tcp connection to 203.78.103.109.
Duration: 2h 42 min.
IOC's
- IP : 194.61.24.102 (Attacker)
- IP : 203.78.103.109 (C2 server)
- MD5 : eed41b4500e473f97c50c7385ef5e374 (coreupdater.exe)
- JA3 Hash : 84fef6113e562e7cc7e3f8b1f62c469b (RDP scan/brute force)
- JA3 Hash : 6dc99de941a8f76cad308d9089e793d7 (RDP scan/brute force)
- JA3 Hash : e26ff759048e07b164d8faf6c2a19f53 (RDP scan/brute force)
- JA3 Hash : 3bdfb64d53404bacd8a47056c6a756be (RDP scan/brute force)
Wanna learn more network forensic analysis techniques? Then check out our upcoming network forensics classes in September and October.
Posted by Erik Hjelmvik on Friday, 09 July 2021 13:20:00 (UTC/GMT)
Tags: #PCAP #NetworkMiner #CapLoader #video #videotutorial



