10 Years of NetworkMiner
I released the first version of NetworkMiner on February 16, 2007, which is exactly 10 years ago today.
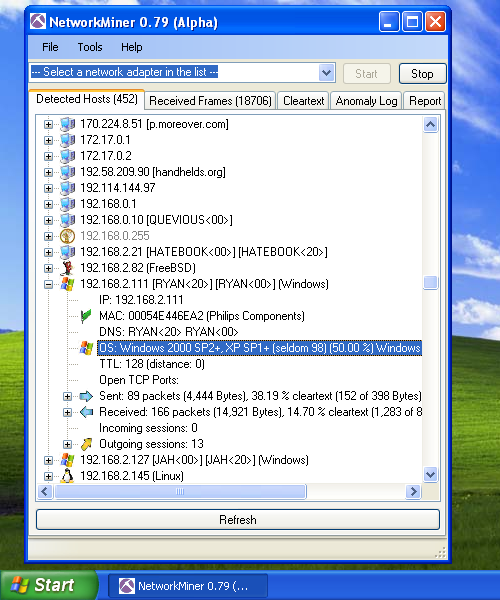
One of the main uses of NetworkMiner today is to reassemble file transfers from PCAP files and save the extracted files to disk. However, as you can see in the screenshot above, the early versions of NetworkMiner didn’t even have a Files tab. In fact, the task that NetworkMiner was originally designed for was simply to provide an inventory of the hosts communicating on a network.
How it all started
So, why did I start designing a passive asset detection system when I could just as well have used a port scanner like Nmap to fingerprint the devices on a network? Well, I was working with IT security at the R&D department of a major European energy company at the time. As part of my job I occasionally performed IT security audits of power plants. During these audits I typically wanted to ensure that there were no rouge or unknown devices on the network. The normal way of verifying this would be to perform an Nmap scan of the network, but that wasn’t an option for me since I was dealing with live industrial control system networks. I knew from personal experience that a network scan could cause some of the industrial control system devices to drop their network connections or even crash, so active scanning wasn’t a viable option. Instead I chose to setup a SPAN port at a central point of the network, or even install a network TAP, and then capture network traffic to a PCAP file during a few hours. I found the PCAP files being a great source, not only for identifying the hosts present at a network, but also in order to discover misconfigured devices. However, I wasn’t really happy with the tools available for visualizing the devices on the network, which is why I stated developing NetworkMiner in my spare time.
Network Forensics
As I continued improving NetworkMiner I pretty soon ended up writing my own TCP reassembly engine as well as parsers for HTTP and the CIFS protocol (a.k.a SMB). With these protocols in place I was able to extract files downloaded through HTTP or SMB to disk with NetworkMiner, which turned out to be a killer feature.
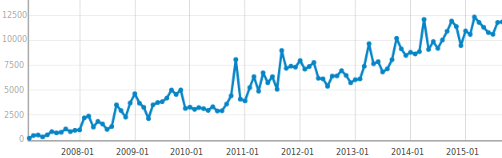
Image: Monthly downloads of NetworkMiner from SourceForge
With the ability to extract file transfers from PCAP files NetworkMiner steadily gained popularity as a valuable tool in the field of network forensics, which motivated me to make the tool even better. Throughout these past 10 years I have single-handedly implemented over 60 protocols in NetworkMiner, which has been a great learning experience for me.
NetworkMiner Milestones
- 2007-02-16 First release of NetworkMiner on SourceForge
- 2008-08-01 NetworkMiner is featured in Russ McRee’s toolsmith column for August 2008.
- 2008-09-01 Richard Bejtlich blogs about NetworkMiner 0.85 on the TaoSecurity blog
- 2011-03-04 First release of NetworkMiner Professional and the command line version NetworkMinerCLI.
- 2011-11-11 NetworkMiner ranked #85 among SecTools.Org’s “Top 125 Network Security Tools”
- 2011-11-19 Cross platform support (works in Linux, Mac OSX etc).
- 2011-12-16 REMnux Linux distro includes NetworkMiner
- 2011-12-27 Security Onion Linux distro includes NetworkMiner
- 2013-09-15 Support for PcapNG capture file format in NetworkMiner Professional 1.5
- 2016-02-19 Project hosting moved from SourceForge to netresec.com
Looking Forward
People sometimes ask me what I’m planning to add to the next version of NetworkMiner. To be honest; I never really know. In fact, I’ve realized that those with the best ideas for features or protocols to add to NetworkMiner are those who use NetworkMiner as part of their jobs, such as incident responders and digital forensics experts across the globe.
I therefore highly value feedback from users, so if you have requests for new features to be added to the next version, then please feel free to reach out and let me know!
Posted by Erik Hjelmvik on Thursday, 16 February 2017 09:11:00 (UTC/GMT)
Tags: #Netresec #NetworkMiner #NSM #ICS



