RawCap
RawCap is a free command line network sniffer for Windows that uses raw sockets.
Quick RawCap facts:
- Can sniff any interface that has got an IPv4 address, including 127.0.0.1 (localhost/loopback)
- RawCap.exe is just 48 kB
- No external libraries or DLL's needed other than .NET Framework
- No installation required, just download RawCap.exe and sniff
- Captures from any type of network, including WiFi, VPN, WWAN (Mobile Broadband) and PPP interfaces
- Simple to use
Usage
You will need administrator privileges to run RawCap.
NETRESEC RawCap version 0.2.0.0
Usage: RawCap.exe [OPTIONS] <interface> <pcap_target>
<interface> can be an interface number or IP address
<pcap_target> can be filename, stdout (-) or named pipe (starting with \\.\pipe\)
OPTIONS:
-f Flush data to file after each packet (no buffer)
-c <count> Stop sniffing after receiving <count> packets
-s <sec> Stop sniffing after <sec> seconds
-m Disable automatic creation of RawCap firewall entry
-q Quiet, don't print packet count to standard out
INTERFACES:
0. IP : 169.254.63.243
NIC Name : Local Area Connection
NIC Type : Ethernet
1. IP : 192.168.1.129
NIC Name : WiFi
NIC Type : Wireless80211
2. IP : 127.0.0.1
NIC Name : Loopback Pseudo-Interface 1
NIC Type : Loopback
3. IP : 10.165.240.132
NIC Name : Mobile 12
NIC Type : Wwanpp
Example 1: RawCap.exe 0 dumpfile.pcap
Example 2: RawCap.exe -s 60 127.0.0.1 localhost.pcap
Example 3: RawCap.exe 127.0.0.1 \\.\pipe\RawCap
Example 4: RawCap.exe -q 127.0.0.1 - | Wireshark.exe -i - -k
An alternative to supplying the interface number is to supply the IP address of the preferred interface instead, i.e. like this:
Interactive Console Dialog
You can also start RawCap without any arguments, this will leave you with an interactive dialog:
Network interfaces:
0. 192.168.0.17 Local Area Connection
1. 192.168.0.47 Wireless Network Connection
2. 90.130.211.54 3G UMTS Internet
3. 192.168.111.1 VMware Network Adapter VMnet1
4. 192.168.222.1 VMware Network Adapter VMnet2
5. 127.0.0.1 Loopback Pseudo-Interface
Select network interface to sniff [default '0']: 1
Output path or filename [default 'dumpfile.pcap']:
Sniffing IP : 192.168.0.47
Output File : dumpfile.pcap
--- Press [Ctrl]+C to stop ---
Packets : 1337
Streaming PCAP to Wireshark
The easiest way to analyze packets captured by RawCap in Wireshark is to save them to a capture file and open it in Wireshark. But you can also use alternative output methods to analyze the captured packets using Wireshark in real-time.
The simplest way to analyze packets in real-time is to write the PCAP data to standard output (stdout) using the "-" switch, and then reading that data in Wireshark with the "-i -" switch.
Another alternative is to write the PCAP data to a named pipe, and then let Wireshark "sniff" packets from that named pipe.
-
Start RawCap and let it write PCAP data to a named pipe called "RawCap". RawCap.exe 127.0.0.1 \\.\pipe\RawCap
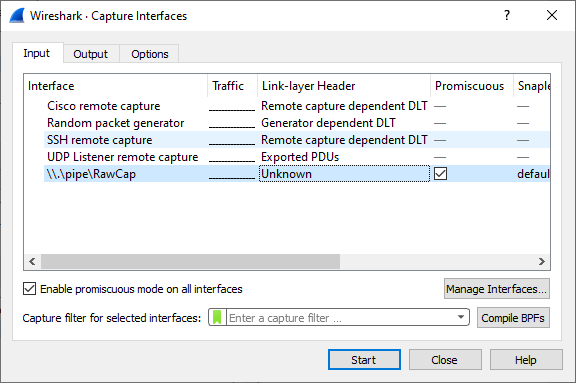
- Start Wireshark (version 2.3.0 or later)
- Click: Capture > Options
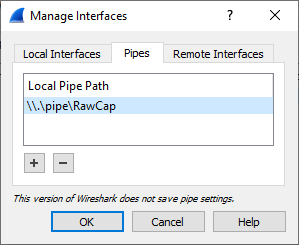
- Click "Manage Interfaces..."
- Select the "Pipes" tab
- Click the "+" button to add a named pipe
- Name the pipe "\\.\pipe\RawCap" and press ENTER to save it
- Click "OK" in the Manage Interface window
- Click "Start" to see the packets sniffed by RawCap in real-time
Old vs. New RawCap Version
The new RawCap versionis better than the previous version in many ways, but there are a couple of drawbacks. We therefore let the user choose which version to download.
| RawCap 0.1.5.0 (old) | RawCap 0.2.1.0 (new) | |
|---|---|---|
| Release year | 2013 | 2022 |
| Save packets in PCAP file | ✅ | ✅ |
| Write packets to standard output (stdout) | ✅ | |
| Write packets to named pipe | ✅ | |
| Automatic firewall configuration | ✅ | |
| Capture from any IPv4 address | ✅ | ✅ |
| IPv6 support | ||
| Target .NET framework | .NET Framework 2.0 | .NET Framework 4.7.2 |
| File size | 23 kB | 54 kB |
| Download Old Version | Download New Version |
Raw sockets limitations (OS dependent)
IPv6
RawCap cannot capture packets from IPv6 interfaces. This also include the localhost IPv6 interface associated with address ::1. Unfortunately the name "localhost" often resolves to ::1 rather than 127.0.0.1, which can cause confusion. Therefore, when trying to capture application traffic on localhost, make sure the monitored application is connecting to "127.0.0.1" rather than "localhost".
Sniffing localhost
Sniffing localhost/loopback (127.0.0.1) has some limitations under Windows XP.
When sniffing localhost traffic in Windows XP you will only be able to capture UDP and ICMP packets, not TCP.
TCP, UDP and ICMP packets can, however, all be sniffed properly from localhost on newer operating systems like Windows Vista and Windows 7.
External interfaces
Windows Vista can't capture outgoing packets, only incoming.
If you, on the other hand, find that you are only able to sniff OUTGOING packets then you probably just need to add an exception for RawCap in your local firewall. To create an exception, simply follow these steps:
- Run WF.msc (i.e. the "Windows Firewall with Advanced Security")
- Select "Inbound Rules"
- Click "New Rule"
- Select "Program" and click "Next"
- Enter the path of RawCap.exe and click "Next"
- Click "Next" a couple of times more, then you're done!
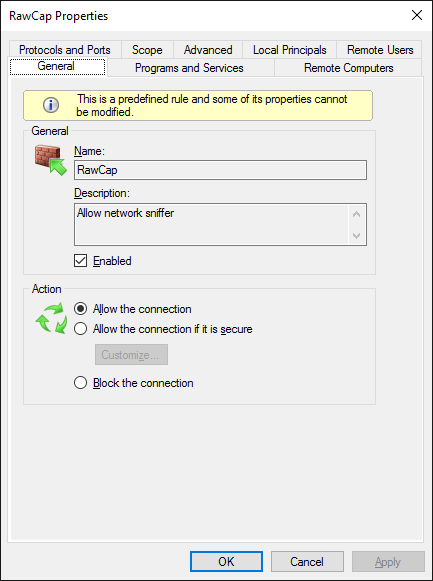
Firewall rule to allow RawCap to sniff incoming packets.
Gigantic Packets due to Offloading
If you get a SocketException saying something like "the buffer used to receive a datagram into was smaller than the datagram itself", then you probably have Large Send Offload (LSO) enabled on your network interface. This feature is also known as TCP Segmentation Offload (TSO) and is used to reduce CPU overhead for packet processing, in particular on virtual machines.
Newer versions of RawCap will print the following error message when a too large packet is received:
You can disable LSO by changing the value for "Large Send Offload V2 (IPv4)" in the network adapter's advanced settings, as show in this screenshot:
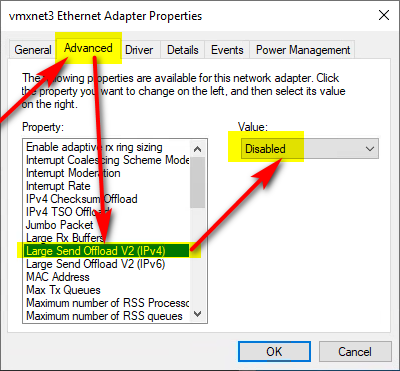
Image credit: Rene Perraux
LSO can also be dissabled programmatically using PowerShell:
Adding Fake Ethernet Headers
PCAP files created with RawCap use the "DLT_RAW" aka "RAW_IP" encapsulation type. This means that all frames in the capture file start with an IP header instead of, for example, an Ethernet header. Unfortunately not all tools support the Raw IP encap type. But you can prepend a fake Ethernet header to all frames in a PCAP file by using tcprewrite like this:
License
RawCap is freeware and can be used by anyone, i.e. even commercial use is allowed.
You are, however, NOT allowed to:
- Re-brand RawCap under a different name or vendor
- Re-distribute RawCap from a website other than netresec.com
- Sell RawCap
- Include RawCap as part of a commercial tool
More information
You can read more about RawCap in our blog posts "RawCap sniffer for Windows released" (2011) and "RawCap Redux" (2020). As well as other blog posts tagged with RawCap.

