NetworkMiner 2.8.1 Released
I am happy to announce the release of NetworkMiner 2.8.1 today!

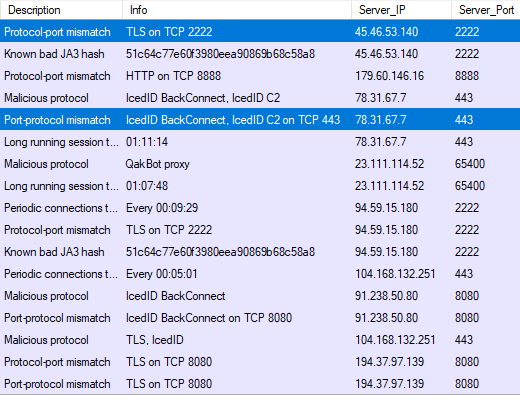
This new release brings a VNC parser to NetworkMiner, so that screenshots, keystrokes and clipboard data can be extracted from unencrypted VNC traffic. NetworkMiner 2.8.1 additionally includes parsers for command-and-control (C2) protocols used by njRAT, IcedID, QakBot and Bazar. We have also added extraction of files sent using a HTTP PUT request, which is the rare cousin to the more common POST request. NetworkMiner’s Images tab has also been updated to enable filtering based on filename or pixel count.
VNC
NetworkMiner now supports the remote framebuffer (RFB) protocol (RFC 6143), which is the underlying protocol used in VNC software. VNC is used to remotely control another computer with help of a real-time video feed of the remote computer’s screen and the ability to control the remote desktop using a mouse and keyboard.
NetworkMiner reassembles the desktop graphics that get transferred between a VNC client and server to build a local representation of the remote desktop. Screenshots of that desktop then get extracted to disk by NetworkMiner as it gets updated. These desktop screenshots can be viewed in NetworkMiner’s Images tab. NetworkMiner also extracts keystrokes and clipboard data from the VNC traffic and displays them in the Parameters tab.
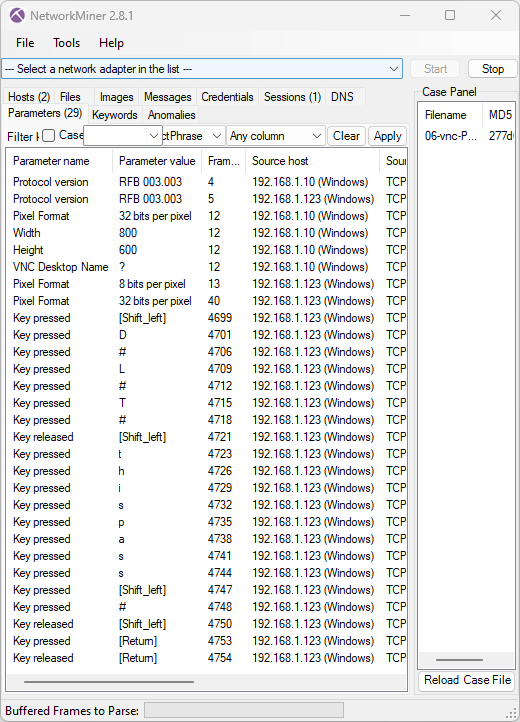
Image: Keystrokes “D#L#T#thispass#” extracted from 06-vnc-Password-3.3.pcap, which is available in “vnc-pcaps.zip” from the Openwall Wiki
Limitations in VNC Extraction
Essential configuration of the VNC session is set up in the beginning of each TCP session. NetworkMiner therefore requires analyzed traffic to include this initial setup in order to successfully extract graphics from a VNC session.
Only traffic to TCP ports 5900 and 5901 will be parsed as VNC traffic by the free version of NetworkMiner. Our commercial tool NetworkMiner Professional has the ability to identify VNC traffic regardless of port number, but the free version will fail to extract screenshots from VNC traffic running on non-standard ports.
NetworkMiner’s VNC implementation is currently at an early stage, which is why it might fail to extract screenshots or other data from VNC sessions. If you encounter VNC traffic that NetworkMiner fails to parse, then we’d be very grateful if you would contact us and let us know so that we can improve NetworkMiner’s VNC extraction in future releases.
BackConnect
I have previously outlined the BackConnect protocol used by IcedID, QakBot as well as Bazar. This BackConnect protocol is used by botnet operators to remotely control a victim computer using a form of remote access trojan (RAT). This BackConnect protocol supports features such as tunneling network traffic through the victim’s computer, uploading files and the ability to control the victim’s computer using VNC.
NetworkMiner now has a parser for this BackConnect protocol, which allows analysts to see screenshots, keystrokes and file uploads from when the attacker interacts with the hacked computer. As you might have guessed, NetworkMiner’s VNC parser is reused in order to also parse reverse VNC traffic from BackConnect sessions.
I would like to thank Maxime Thiebaut for releasing his PCAPeek tool, which also reassembles reverse VNC traffic from BackConnect traffic. Maxime’s tool proved that it was possible to extract graphics from this C2 traffic, which motivated me to create a BackConnect VNC parser for NetworkMiner.
BackConnect VNC Replay
To demonstrate NetworkMiner’s reverse VNC reassembly I’d like to use the file “2023-07-26-IcedID-with-Keyhole-VNC-traffic.pcap” from Brad Duncan’s fantastic malware-traffic-analysis.net website. In this traffic the IcedID BackConnect C2 server listens to TCP port 443 on 165.232.175.216.
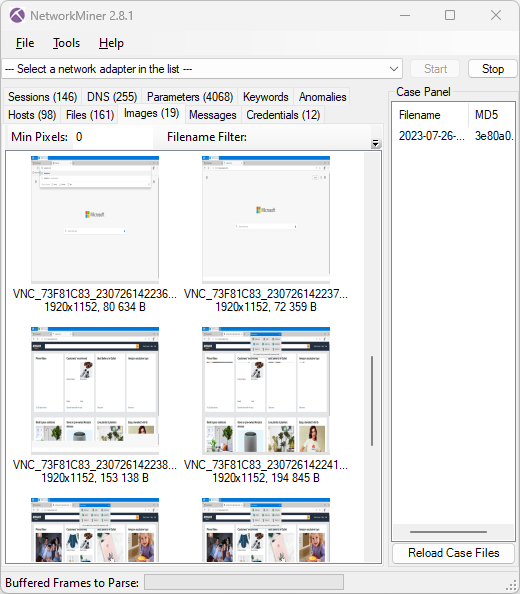
Image: NetworkMiner showing thumbnails of extracted screenshots
The screenshot thumbnails from the BackConnect VNC traffic shows that the attacker opens up the Amazon website on the victim’s computer. A copy of the full 1920x1152 screenshot, which NetworkMiner extracted from the VNC traffic, can be viewed here: VNC_73F81C83_230726142247.jpg
The parameters tab in NetworkMiner additionally confirms that the attacker manually typed “amazon.com” into the hacked computer’s web browser.
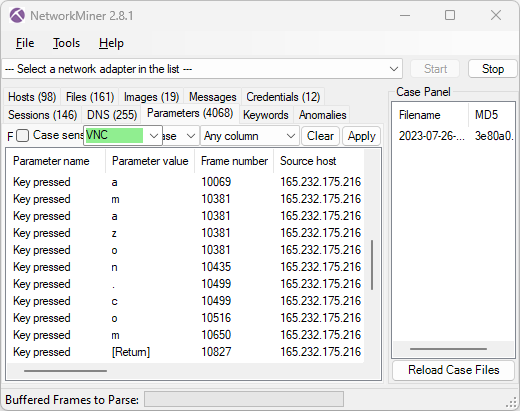
Image: Keylog of attacker typing amazon.com
Limitations in BackConnect Parser
The BackConnect implementation in NetworkMiner 2.8.1 is pretty well tested and even supports the new “encrypted” version of BackConnect that IcedID has been deploying lately (we call it “BackConnect XOR”). NetworkMiner can parse the BackConnect C2 traffic as well as the traffic from modules for reverse VNC, reverse SOCKS, reverse shell and the file manager.
Unfortunately the BackConnect traffic typically runs on TCP ports like 443 or 8080, which are normally used for TLS or web proxies. The free open source version of NetworkMiner normally attempts to interpret traffic to port 443 as TLS and 8080 as HTTP proxy, even though it might be BackConnect. A hardcoded list of 32 verified BackConnect C2 servers, such as 165.232.175.216:443, 137.184.172.23:443 and 185.99.132.16:8080, has therefore been added to NetworkMiner’s source code. This enables NetworkMiner to interpret traffic to those IP:port combinations as BackConnect. Our commercial tool NetworkMiner Professional can identify protocols without relying on the port number though, this enables the “Pro” version to also parse BackConnect traffic to C2 servers that aren’t among the 32 hard coded ones in the source code.
njRAT
njRAT is an old, yet still very popular remote access trojan (RAT). It has been around for at least 10 years (since 2013) and can be used to do things like:
- Steal credentials
- Take screenshots of the desktop
- Start the camera
- Record audio with the microphone
- Start a reverse shell
- Upload or download files
- Execute a file or module
- Capture keystrokes with a keylogger
- Create, read or delete registry keys
- Run a command
I have been teaching students in my network forensics classes how to manually parse njRAT traffic since 2015, but from now on I’ll instead be able to tell them to load the njRAT traffic into NetworkMiner to see what the attacker did on the victim’s computer.
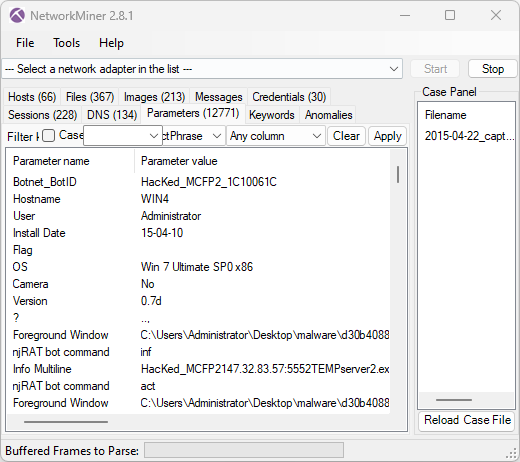
Image: Information extracted from njRAT C2 traffic by NetworkMiner
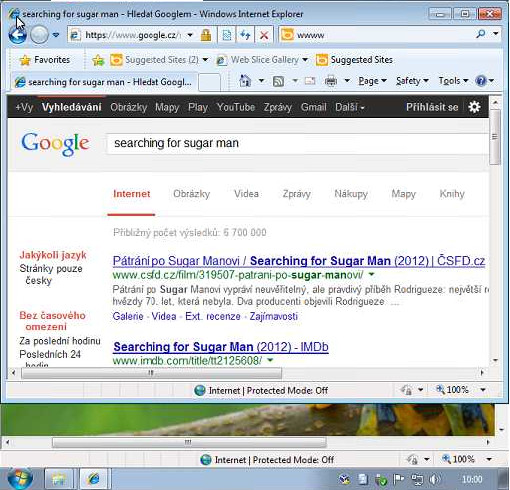
Image: Screenshot of infected computer extracted from njRAT C2 traffic
The NetworkMiner parameters and victim PC screenshot above were extracted from 2015-04-22_capture-win4.pcap in StratosphereIPS’ dataset CTU-Malware-Capture-Botnet-120-1. The victim PC desktop screenshot actually came out as a 51x4900 pixel image in NetworkMiner 2.8.1, so I had to manually reorganize the tiles to a 510x490 image instead. I’m planning to add an automatic retiling feature to NetworkMiner to avoid having to do this manually in the future.
Limitations in njRAT Parser
njRAT comes in many different versions, forks and flavors and the protocol even has a field delimiter sequence that can be customized for each njRAT backdoor. I can therefore not guarantee that NetworkMiner will be able to parse traffic from all njRAT sessions, but so far I’ve seen very good results – even when custom field delimiters are being used.
Nevertheless, this trojan has an abundance of features but only the most commonly used ones are implemented in NetworkMiner. More specifically NetworkMiner primarily supports extraction of screenshots, credentials, keylog data, file uploads and downloads. NetworkMiner also extracts exfiltrated metadata about the victim machine and bot, such as the hostname, operating system, logged in user, bot ID, botnet, njRAT version and njRAT install date.
Also, as previously mentioned, NetworkMiner doesn’t yet stitch together tiles of desktop screenshots correctly.
Another limitation is that an njRAT C2 server can be deployed on any TCP port, which might prevent the free version from interpreting the C2 traffic as njRAT. The free version of NetworkMiner currently tries to parse traffic to ports like 1177, 5050, 5552 and a few others as njRAT, while NetworkMiner Professional will automatically recognize the njRAT protocol regardless which port it runs on.
Bug Fixes
We’ve added support for SIP keepalive messages (RFC 5626) in NetworkMiner 2.8.1. NetworkMiner Professional would previously fail to extract VoIP calls, or text messages sent through SIP, if a keepalive packet was sent in the session prior to the call or text message. We have also fixed a bug in NetworkMiner’s CapWap parser.
Upgrading to Version 2.8.1
Users who have purchased NetworkMiner Professional can download a free update to version 2.8.1 from our customer portal, or use the “Check for Updates” feature from NetworkMiner's Help menu. Those who instead prefer to use the free and open source version can grab the latest version of NetworkMiner from the official NetworkMiner page.
Posted by Erik Hjelmvik on Monday, 02 October 2023 11:13:00 (UTC/GMT)
Tags: #NetworkMiner #VNC #BackConnect #IcedID #njRAT