Erik Hjelmvik
,
Thursday, 14 November 2019 12:25:00 (UTC/GMT)

NetworkMiner is one of the best tools around for extracting credentials, such as usernames and passwords, from PCAP files.
The credential extraction feature is primarily designed for defenders, in order to analyze
credential theft and
lateral movement by adversaries inside your networks.
But the credential extraction feature is also popular among penetration testers.
In this blog post I will demo how Kerberos hashes can be extracted from captured network traffic with NetworkMiner, and how these hashes can be cracked in order to retrieve the clear text passwords.
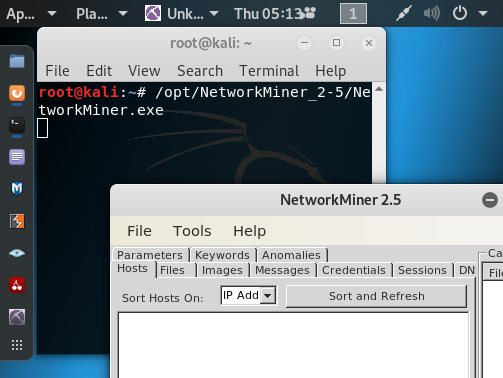
Installing NetworkMiner in Kali Linux
I’m using a clean install of
Kali Linux 2019.3, on which I have installed NetworkMiner by following the step-by-step instructions in our guide for
installing NetworkMiner in Linux.
Extracting Kerberos Hashes from PCAP
There is a capture file in
Wireshark’s sample captures called krb-816.cap.
This capture file contains Kerberos traffic from a Windows XP machine, as two user accounts perform a domain logon.
Let’s download that PCAP file and open it in NetworkMiner.
wget 'https://wiki.wireshark.org/SampleCaptures?action=AttachFile&do=get&target=krb-816.zip' -O krb-816.zip
unzip krb-816.zip
/opt/NetworkMiner_2-5/NetworkMiner.exe krb-816.cap
The “Credentials” tab contains the extracted Kerberos hashes.
Right-click on the first $krb5pa$23$ hash and select “Copy Password” to put the password into the system clipboard.
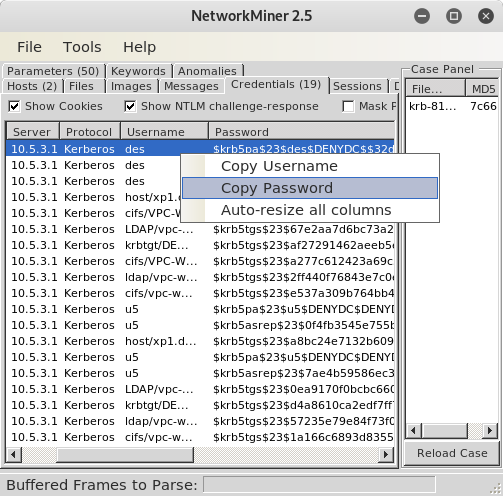
Paste the password to a text file, either using a text editor or directly from a shell.
Note: You'll need to do press Ctrl+Shift+Insert in GNOME Terminal to paste from the system clipboard, which is where NetworkMiner has put the password.
echo '$krb5pa$23$des$DENYDC$$32d396a914a4d0a78e979ba75d4ff53c1db7294141760fee05e434c12ecf8d5b9aa5839e09a2244893aff5f384f79c37883f154a' > krb5pa.hash
You can now try to crack the hash, for example by running John the Ripper (JtR) or hashcat.
john krb5pa.hash
Using default input encoding: UTF-8
Loaded 1 password hash (krb5pa-md5, Kerberos 5 AS-REQ Pre-Auth etype 23 [32/64])
[...]
Use the "--show" option to display all of the cracked passwords reliably
Session completed
john krb5pa.hash --show
?:123
1 password hash cracked, 0 left
Yay! We now know that the password of user “des” was “123”.
Let’s try to recover the password of the user “u5” as well, but this time we’ll use the
$krb5asrep$23$ hash.
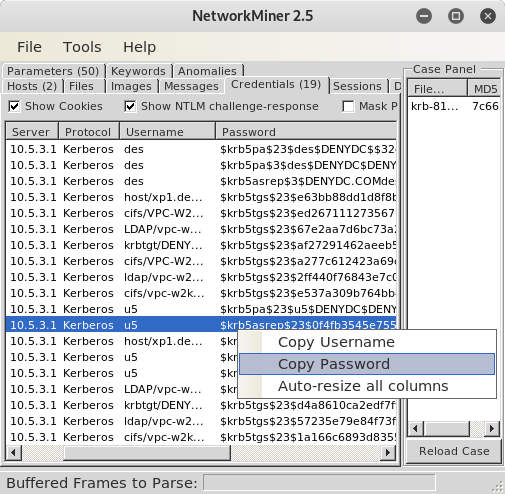
john krb5asrep.hash
[...]
john krb5asrep.hash --show
?:123
1 password hash cracked, 0 left
Apparently the password for user u5 was “123” as well.
If you wanna replace JtR with hashcat, then make sure to use the following hash modes:
- $krb5pa$23$: hashcat -m 7500
- $krb5tgs$23$: hashcat -m 13100
- $krb5asrep$23$: hashcat -m 18200
For other hash types, please see the hashcat example hashes.
Running the Command Line version of NetworkMiner
The commercial version of NetworkMiner comes with a command line tool called
NetworkMinerCLI.
You can extract the Kerberos hashes from a PCAP file and save them to a CSV file using NetworkMinerCLI like this:
/opt/NetworkMinerProfessional_2-5/NetworkMinerCLI.exe -r krb-816.cap -f CSV_NoNewlines
Closing file handles...
32 frames parsed in 0.1337 seconds.
NetworkMinerCLI has now created a set of CSV files, one for each type/class of information found in the capture file.
In this case we want the
krb-816.cap.Credentials.csv file,
in which the hashes and passwords are in column 5:
cut -d, -f5 krb-816.cap.Credentials.csv
"Password"
"$krb5pa$23$des$DENYDC$$32d396a914a4d0a78e979ba75d4ff53c1db7294141760fee05e434c12ecf8d5b9aa5839e09a2244893aff5f384f79c37883f154a"
"$krb5pa$3$des$DENYDC$DENYDC.COMdes$233b4272aa93727221facfdbdcc9d1d9a0c43a2798c810600310c0daf48fb969c26cb47d69f575a65e00163845f68811f9c5266271cc0f91"
"$krb5asrep$3$DENYDC.COMdes$edbcc0d67f3a645254f086e6$e2bfe2b7bbac72b346ad05abb8326f6d684dcb52b6c2f446921417579e038103eb2e9039aa3a2db85c8e1afc2ed56130b4855834725096edb74d1582920b3b1b7e30ef51b14c8977487147b868c3e0f7c3e8c5d5618b9dfa0fd90e62c35f8bd41ab283d87155cd51a01b8ced6411f1f0e060d9b4a78de2afc281756a0030453418d263784f91725387d7469820904b646ac519384f24d6ff769b7af8594c8a02c0cf691d38bf115b588848ed7acf5ac7fae159a13590094fc199d85522a97c4213cc68845023c7f12f7da9e7623e4ed0241ad1145418b3cc373dc59c71b6cafec370557816f949c736497f12313fd76d4eeffc9ded11605fe52e8171fa6026d68f1ade93"
[...]
Posted by Erik Hjelmvik on Thursday, 14 November 2019 12:25:00 (UTC/GMT)
Tags: #PCAP
#Kerberos
#Kali
#Linux
#hashcat
#John
#JtR
#NetworkMinerCLI










