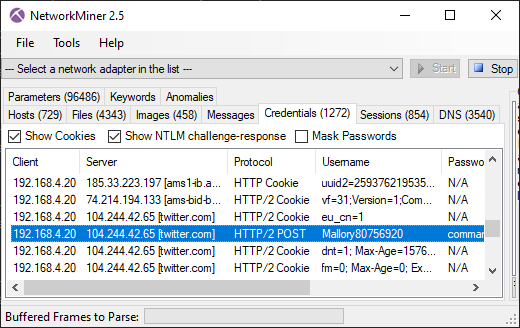
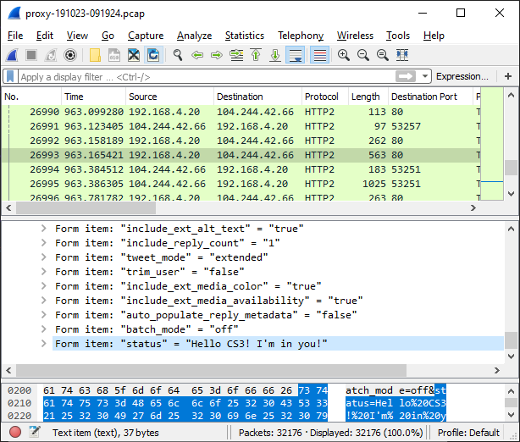
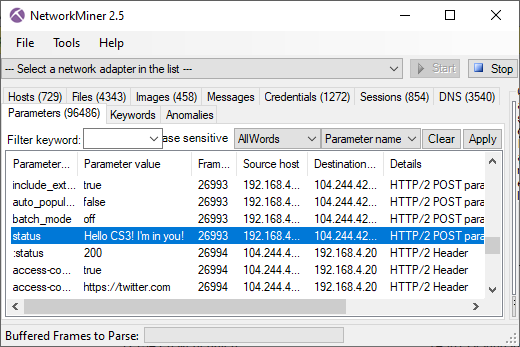
Discovered Artifacts in Decrypted HTTPS
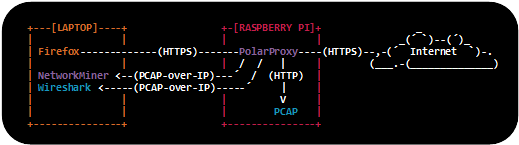
We released a PCAP file earlier this year, which was recorded as part of a live TLS decryption demo at the CS3Sthlm conference. The demo setup used PolarProxy running on a Raspberry Pi in order to decrypt all HTTPS traffic and save it in a PCAP file as unencrypted HTTP.
This capture file was later used as a challenge for our twitter followers, when we made the following announcement:
PCAP CHALLENGE!
The capture file released in this blog post contains a few interesting things that were captured unintentionally. Can you find anything strange, funny or unexpected in the pcap file? (1/2)
Followed by this message:
The person to submit the most interesting answer wins a “PCAP or it didn’t happen” t-shirt. Compete by including your discovery in a retweet or reply to this tweet, or in an email to info(at)netresec.com. We want your answers before the end of January. (2/2)
We'd like to thank everyone who submitted answers in this challenge, such as David Ledbetter, Christoffer Strömblad, RunΞ and Chris Sistrunk.
We're happy to announce that the winner of our challenge is David Ledbetter. Congratulations David!
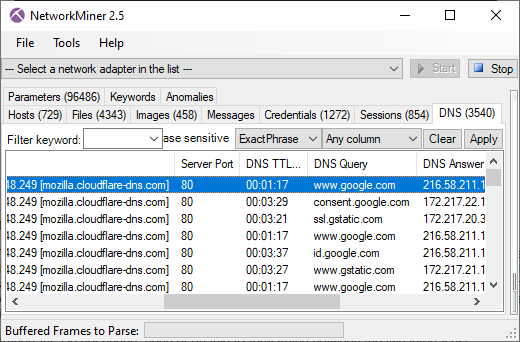
So what were the interesting thing that could be found in the released capture file? Below is a short summary of some things that can be found.
Telemetry data sent to mozilla.org
A surprising amount of information about the Firefox browser was sent to
- Active browser addons
- Active browser plugins
- Firefox profile creation date
- Browser search region
- Default search engine
- Regional locales
- Screen width
- Screen height
- CPU vendor, family and model
- HDD model, revision and type
- Installed RAM
- Operating system
- Etc..
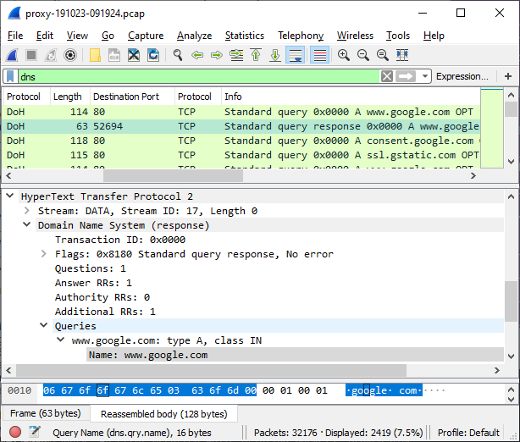
Here's an excerpt showing a part of the data sent to Mozilla:
"build": { "applicationId": "{ec8030f7-c20a-464f-9b0e-13a3a9e97384}", "applicationName": "Firefox", "architecture": "x86-64", "buildId": "20191002194346", "version": "69.0.2", "vendor": "Mozilla", "displayVersion": "69.0.2", "platformVersion": "69.0.2", "xpcomAbi": "x86_64-gcc3", "updaterAvailable": false }, "partner": { "distributionId": "canonical", "distributionVersion": "1.0", "partnerId": "ubuntu", "distributor": "canonical", "distributorChannel": "ubuntu", "partnerNames": [ "ubuntu" ] }, "system": { "memoryMB": 3943, "virtualMaxMB": null, "cpu": { "count": 1, "cores": 1, "vendor": "GenuineIntel", "family": 6, "model": 42, "stepping": 7, "l2cacheKB": 256, "l3cacheKB": 4096, "speedMHz": null, "extensions": [ "hasMMX", "hasSSE", "hasSSE2", "hasSSE3", "hasSSSE3", "hasSSE4_1", "hasSSE4_2", "hasAVX", "hasAES" ] }, "os": { "name": "Linux", "version": "5.0.0-31-generic", "locale": "en-US" }, "hdd": { "profile": { "model": null, "revision": null, "type": null }, "binary": { "model": null, "revision": null, "type": null }, "system": { "model": null, "revision": null, "type": null } }, "gfx": { "D2DEnabled": null, "DWriteEnabled": null, "ContentBackend": "Skia", "Headless": false, "adapters": [ { "description": "llvmpipe (LLVM 8.0, 256 bits)", "vendorID": "0xffff", "deviceID": "0xffff", "subsysID": null, "RAM": 3942, "driver": null, "driverVendor": "mesa/llvmpipe", "driverVersion": "19.0.8.0", "driverDate": null, "GPUActive": true } ], "monitors": [ { "screenWidth": 681, "screenHeight": 654 } ], "features": { "compositor": "basic", "gpuProcess": { "status": "unavailable" }, "wrQualified": { "status": "blocked-vendor-unsupported" }, "webrender": { "status": "opt-in" } } }, "appleModelId": null }, "settings": { "blocklistEnabled": true, "e10sEnabled": true, "e10sMultiProcesses": 8, "telemetryEnabled": false, "locale": "en-US", "intl": { "requestedLocales": [ "en-US" ], "availableLocales": [ "en-US", "en-CA", "en-GB" ], "appLocales": [ "en-US", "en-CA", "en-GB", "und" ], "systemLocales": [ "en-US" ], "regionalPrefsLocales": [ "sv-SE" ], "acceptLanguages": [ "en-US", "en" ] }, "update": { "channel": "release", "enabled": true, "autoDownload": false }, "userPrefs": { "browser.cache.disk.capacity": 1048576, "browser.search.region": "SE", "browser.search.widget.inNavBar": false, "network.trr.mode": 2 }, "sandbox": { "effectiveContentProcessLevel": 4 }, "addonCompatibilityCheckEnabled": true, "isDefaultBrowser": false, "defaultSearchEngine": "google", "defaultSearchEngineData": { "name": "Google", "loadPath": "[distribution]/searchplugins/locale/en-US/google.xml", "origin": "default", "submissionURL": "https://www.google.com/search?client=ubuntu&channel=fs&q=&ie=utf-8&oe=utf-8" } }, "profile": { "creationDate": 18183, "firstUseDate": 18183 }
You can use the following Wireshark display filter to find all the data sent to Mozilla:
http.request.method eq POST and http.host contains telemetry
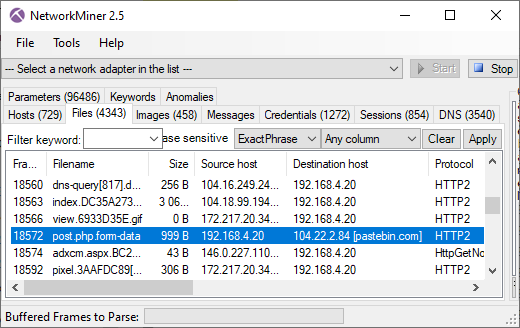
Public IP Revealed in PCAP
The client's IP address was 192.168.4.20, which is part of the RFC 1918 192.168/16 private address space.
It's therefore safe to assume that the client was behind a NAT (the client was in fact behind a double NAT).
However, we noticed that the public IP of the client was revealed through multiple services in the captured network traffic.
One of these services is the advertising exchange company AppNexus (adnxs.com), which sent the client's public IP address 193.235.19.252 in an
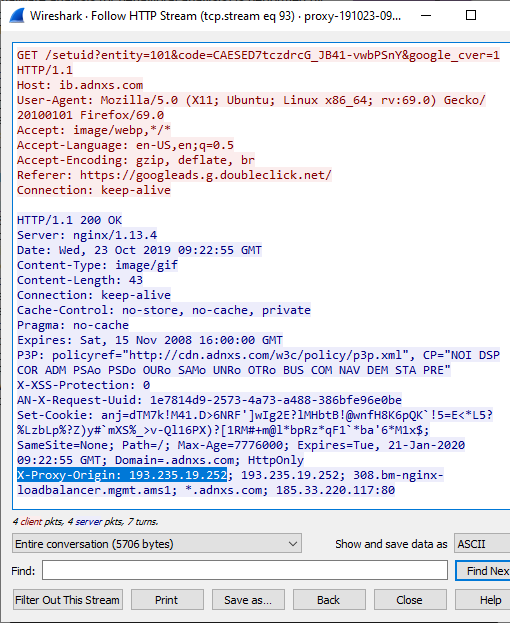
You can use the following Wireshark/tshark display filter to find
http.response.line matches "x-proxy-origin" or http2.header.name matches "x-proxy-origin"
We are using the "matches" operator here instead of "contains" or "==" because we want to perform case insensitive matching. You might also notice that we need a completely different display filter syntax to match HTTP/2 headers compared to what we are used to with HTTP/1.1.
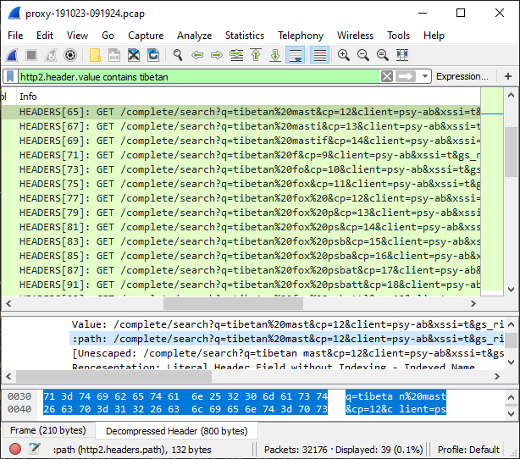
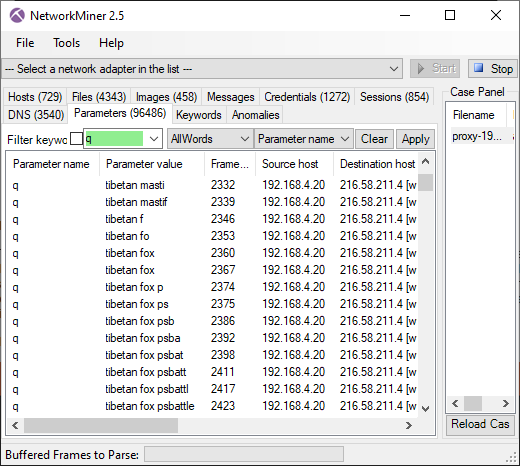
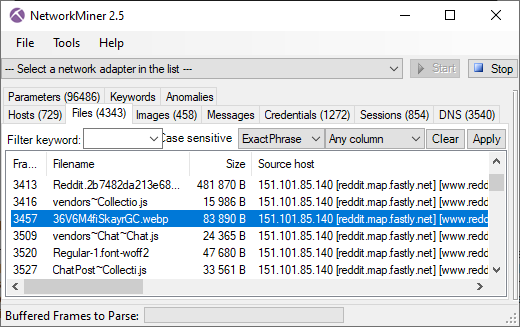
Monty Python "Majestik møøse" reference in reddit x-header
The reddit server 151.101.85.140 sends an HTTP/2 header called "x-moose" with a value of "majestic".
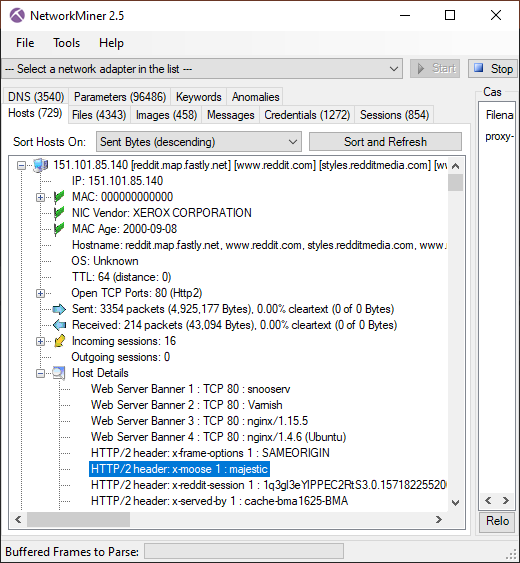
This header refers to the opening credits of Monty Python and the Holy Grail.
Wi nøt trei a høliday in Sweden this yër?
Posted by Erik Hjelmvik on Tuesday, 17 March 2020 09:00:00 (UTC/GMT)
Tags: #HTTP/2 #http2 #TLS #decrypt #TLSI #PolarProxy #NetworkMiner #Wireshark #CS3Sthlm #CS3 #Forensics #PCAP #ASCII-art #RFC1918