Erik Hjelmvik
,
Tuesday, 22 August 2017 11:37:00 (UTC/GMT)

NetworkMiner 2.2 is faster, better and stronger than ever before!
The PCAP parsing speed has more than doubled and even more details are now extracted from analyzed packet capture files.
The improved parsing speed of NetworkMiner 2.2 can be enjoyed regardless if NetworkMiner is run in Windows or
Linux,
additionally the user interface is more responsive and flickers way less when capture files are being loaded.
User Interface Improvements
The keyword filter available in the Files, Messages, Sessions, DNS and Parameters tabs has been improved
so that the rows now can be filtered on a single column of choice by selecting the desired column in a
drop-down list. There is also an “Any column” option, which can be used to search for the keyword in all columns.
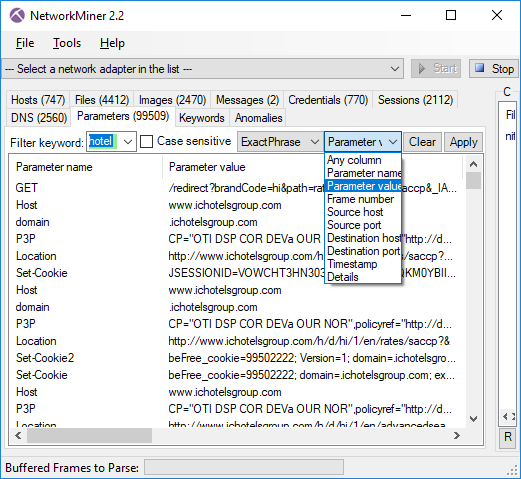
The Messages tab has also received an additional feature, which allows the filter keyword to be matched
against the text in the message body as well as email headers when the “Any column” option is selected.
This allows for an efficient analysis of messages (such as emails sent/received through SMTP, POP3 and
IMAP as well as IRC messages and some HTTP based messaging platforms), since the messages can be filtered
just like in a normal e-mail client.
We have also given up on using local timestamp formats; timestamps are now instead shown using the
yyyy-MM-dd HH:mm:ss format with time zone explicitly stated.
Protocol Parsers
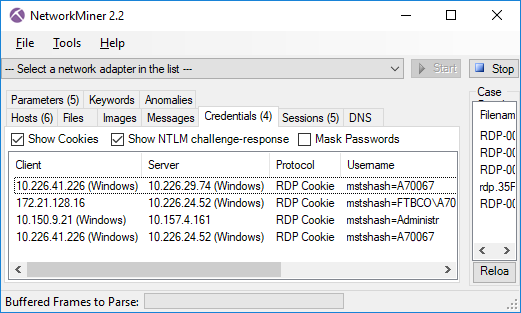
NetworkMiner 2.2 comes with a parser for the Remote Desktop Protocol (RDP), which rides on top of COTP and TPKT.
The RDP parser is primarily used in order to extract usernames from RDP cookies and show them on the Credentials tab.
This new version also comes with better extraction of SMB1 and SMB2 details, such as NTLM SSP usernames.
One big change that has been made behind the scenes of NetworkMiner is the move from .NET Framework 2.0 to version 4.0.
This move doesn’t require any special measures to be taken for most Microsoft Windows users since the 4.0 Framework
is typically already installed on these machines. If you’re running NetworkMiner in Linux, however, you might wanna
check out our updated blog post on
how to install NetworkMiner in Linux.
We have also added an automatic check for new versions of NetworkMiner, which runs every time the tool is started.
This update check can be disabled by adding a --noupdatecheck switch to the command line when starting
NetworkMiner.
NetworkMiner.exe --noupdatecheck capturefile.pcap
NetworkMiner Professional
Even though NetworkMiner 2.2 now uses ISO-like time representations NetworkMiner still has to decide which time zone to use
for the timestamps. The default decision has always been to use the same time zone as the local machine, but
NetworkMiner Professional now additionally comes with an option that allows the user to select whether to use UTC
(as nature intended),
the local time zone or some other custom time zone for displaying timestamps. The time zone setting can be found in the
“Tools > Settings” menu.
UPDATE: With the release of NetworkMiner 2.3 the default time zone is now UTC unless the user has specifically selected a different time zone.
The Port-Independent-Protocol-Detection (PIPI)
feature in NetworkMiner Pro has been improved for more reliable identification of HTTP, SSH, SOCKS, FTP and SSL sessions
running on non-standard port numbers.
CASE / JSON-LD Export
We are happy to announce that the professional edition of NetworkMiner 2.2 now has support for exporting extracted details using the
Cyber-investigation Analysis Standard Expression (CASE) format,
which is a JSON-LD format for digital forensics data. The CASE export is also available in the
command line tool NetworkMinerCLI.
We would like to thank Europol for recommending us to implement the CASE export format in their
effort to adopt CASE as a standard digital forensic format.
Several other companies in the digital forensics field are currently looking into implementing CASE in their tools,
including AccessData, Cellebrite, Guidance, Volatility and XRY.
We believe the CASE format will become a popular format for exchanging digital forensic data between tools for digital forensics,
log correlation and SIEM solutions.
We will, however, still continue supporting and maintaining the CSV and XML export formats in NetworkMiner Professional and
NetworkMinerCLI alongside the new CASE format.
Credits
I would like to thank Sebastian Gebhard and Clinton Page for reporting bugs in the Credentials tab and TFTP parsing code that now have
been fixed. I would also like to thank
Jeff Carrell for providing a
capture file that has been used to debug an
issue in NetworkMiner’s OpenFlow parser. There are also a couple of users who have suggested new features that have made it into this
release of NetworkMiner. Marc Lindike suggested the powerful deep search of extracted messages and
Niclas Hirschfeld proposed a new option in the
PCAP-over-IP functionality
that allows NetworkMiner to receive PCAP data via a remote netcat listener.
Upgrading to Version 2.2
Users who have purchased a license for NetworkMiner Professional 2.x can download a free update to version 2.2 from our
customer portal.
Those who instead prefer to use the free and open source version can grab the latest version of NetworkMiner from the official
NetworkMiner page.
Posted by Erik Hjelmvik on Tuesday, 22 August 2017 11:37:00 (UTC/GMT)
Tags: #pcap
#CASE
#PIPI
#HTTP
#SOCKS
#FTP
#SSL
#port
#forensics

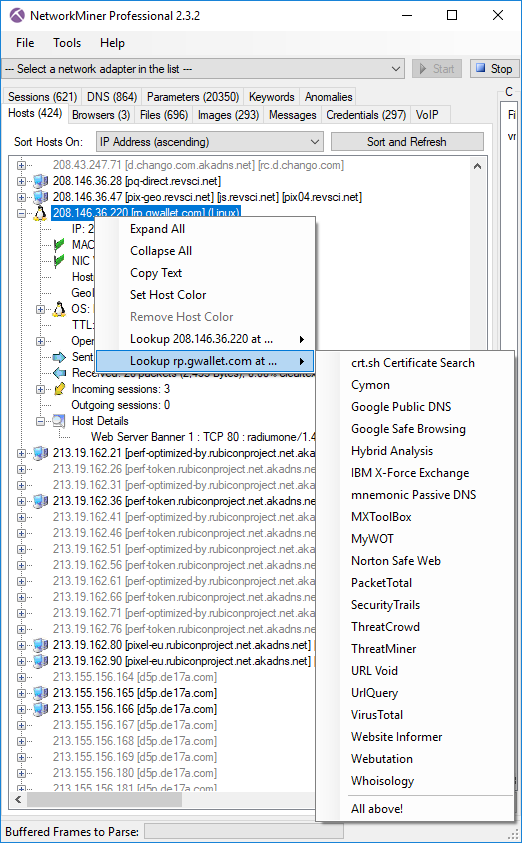 Image: NetworkMiner Professional 2.3.2 with “vm_win7.pcap” from University of Twente’s Data Exfiltration Malware dataset loaded.
Image: NetworkMiner Professional 2.3.2 with “vm_win7.pcap” from University of Twente’s Data Exfiltration Malware dataset loaded.








