Real-time PCAP-over-IP in Wireshark
Did you know that it is possible to stream captured packets from a remote device or application to Wireshark in real-time using PCAP-over-IP? This blog post explains how you can configure Wireshark to read decrypted TLS packets directly from PolarProxy over a TCP socket.
PolarProxy
PolarProxy is a TLS proxy that decrypts and re-encrypts TLS traffic, while also saving the decrypted traffic in a PCAP file. Users who wish to inspect the decrypted TLS traffic in Wireshark typically open this file from disk, but that doesn’t allow for a real-time view of the traffic.
PolarProxy comes with a feature called PCAP-over-IP, which provides a real-time PCAP stream with decrypted packets to connecting clients. If you start PolarProxy with “--pcapoverip 57012” then a PCAP-over-IP listener will be set up on TCP port 57012. I have previously demonstrated how this decrypted stream can be read by NetworkMiner, but it was not until recently that I learned that the same thing can be done with Wireshark as well.
PCAP-over-IP in Wireshark
There’s a little known feature in Wireshark that allows a PCAP stream to be read from a TCP socket, which is exactly what PCAP-over-IP is! To connect to a PolarProxy PCAP-over-IP service on the local PC, do as follows:
- Capture > Options (or Ctrl+K)
- “Manage Interfaces...”
- Select the “Pipes” tab
- Click the “+” button
- Name the pipe “TCP@127.0.0.1:57012” and press ENTER to save it.
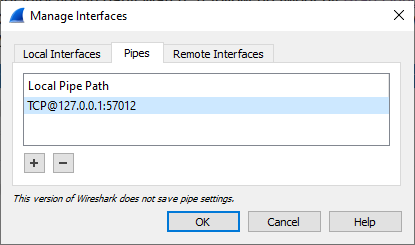
- Click “OK” in the Manage Interface window.
- Click “Start” to inspect decrypted traffic from PolarProxy in real-time.
This setup works on Windows, Linux and macOS. Just remember to replace 127.0.0.1 with the IP of PolarProxy in case it is running on a remote machine.
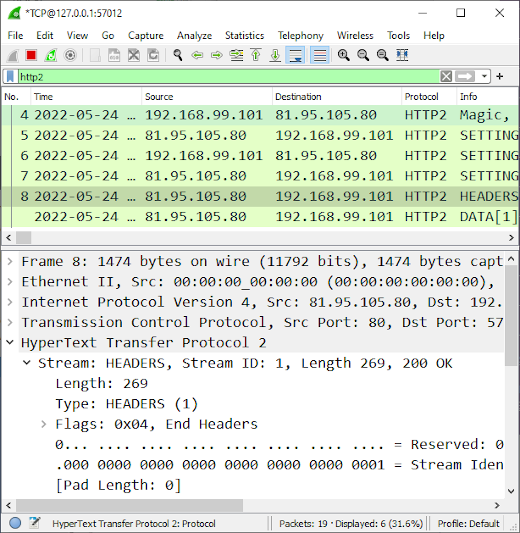
Image: Real-time view of HTTP2 packets from decrypted TLS traffic
It’s also possible to read PCAP-over-IP with the command line tool tshark like this:
The PCAP-over-IP params can also be supplied to Wireshark on the command line in a similar manner:
Happy sniffing!
Posted by Erik Hjelmvik on Tuesday, 24 May 2022 14:00:00 (UTC/GMT)
Tags: #pcapoverip #Wireshark #PolarProxy #PCAP



