Video: TrickBot and ETERNALCHAMPION
This video tutorial is a walkthrough of how you can analyze the PCAP file UISGCON-traffic-analysis-task-pcap-2-of-2.pcap (created by Brad Duncan). The capture file contains a malicious Word Document (macro downloader), Emotet (banking trojan), TrickBot/Trickster (banking trojan) and an EternalChampion (CVE-2017-0146) exploit used to perform lateral movement.
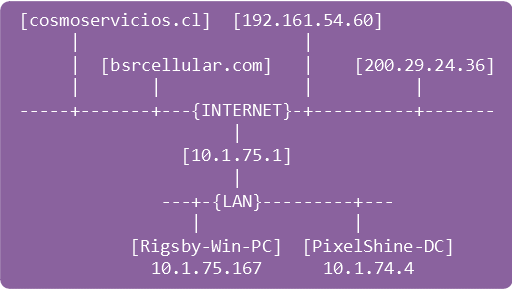
Network Diagram
Timeline of Events
| Frame | Time (UTC) | Event |
|---|---|---|
| 825 | 18:55:32 | Malicious Word doc [cosmoservicios.cl] |
| 1099 | 18:56:04 | Emotet download [bsrcellular.com] |
| 5024 | 19:00:41 | Trickbot "radiance.png" download |
| 9604 | 19:01:34 | Client credentials exfiltrated [200.29.24.36:8082] |
| 9915 | 19:01:36 | ETERNALCHAMPION exploit from client to DC |
| 10424 | 19:01:51 | Client sends .EXE files to \\10.1.75.4\C$\WINDOWS\ |
| 11078 | 19:01:51 | Client infects DC with Trickbot via rogue service |
| 14314 | 19:07:03 | DC credentials exfiltrated [200.29.24.36:8082] |
OSINT Links Opened
- HybridAnalysis: FILE-88654515940798.doc
- VirusTotal: FILE-88654515940798.doc
- VirusTotal: LXHPYOi5j.exe (Emotet)
- HybridAnalysis: LXHPYOi5j.exe (Emotet)
- IBM X-Force Exchange: 87.66.13.80
- VirusTotal: 9b4ui3u2fj1o666n.exe (TrickBot/Trickster)
- VirusTotal: radiance.png (TrickBot/Trickster)
Tools Used
Network Forensics Training
Wanna improve your network forensics skills? Take a look at our trainings, the next scheduled class is on March 18-19 at the TROOPERS conference in Germany.
Posted by Erik Hjelmvik on Wednesday, 23 January 2019 14:00:00 (UTC/GMT)
Tags: #TrickBot #Wireshark #CapLoader #NetworkMiner #videotutorial #video #Emotet #pcap #Network Forensics #ASCII-art



