DFRWS 2009 Network Forensics
I noticed that Juan Leaniz recently posted his analysis of the DFRWS challenge from 2009 on the SANS Computer Forensic Investigations and Incident Response Blog.
I actually submitted a contest entry to this challenge back in 2009, titled "Nothing but Network Forensics". The idea behind my entry was to see just how much information that could be extracted from the pcap files included in the challenge without even looking at the physical memory dump or filesystem images that also were provided as part of the challenge.
I will here provide some highlights from my analysis of the 2009 DFRWS challenge pcap files:
There were two persons involved in the case, I call them "NSSAL" and "JHUISI". I managed to extract the avatar images that were downloaded by these persons when they logged into their online PlayStation accounts.
The actual URL these avatar images were extracted from was http://homeps3.svo.online.scee.com:10060. Yes, that's right, HTTP over TCP port 10060. Extracting these images was much easier to do with NetworkMiner Professional, since it would automatically detect this TCP session as running HTTP with help of the built in port-independent protocol identification feature.
I also used NetworkMiner to see what Google queries that NSSAL performed. By opening the Parameters tab, sorting contents on "Parameter name" column and scrolling down to parameter name "q" i found that NSSAL had searched for:
- mardi gras
- mardi gras pictures
- mardi gras pictures k00l
 The Hosts tab in NetworkMiner also provides more detailed info about the machines involved in this case.
The computer used by NSSAL was actually a PS3 console
(with MAC 001FA7B21ADE) that was running Sony's own CellOS with IP address 137.30.123.78.
The OS fingerprinting feature of NetworkMiner does not contain any OS class for the PS3 CellOS,
the console therefore gets fingerprinted as FreeBSD.
I suppose FreeBSD is quite similar to CellOS since the CellOS is in fact believed to be a branch from the FreeBSD/Darwin development tree.
The Hosts tab in NetworkMiner also provides more detailed info about the machines involved in this case.
The computer used by NSSAL was actually a PS3 console
(with MAC 001FA7B21ADE) that was running Sony's own CellOS with IP address 137.30.123.78.
The OS fingerprinting feature of NetworkMiner does not contain any OS class for the PS3 CellOS,
the console therefore gets fingerprinted as FreeBSD.
I suppose FreeBSD is quite similar to CellOS since the CellOS is in fact believed to be a branch from the FreeBSD/Darwin development tree.
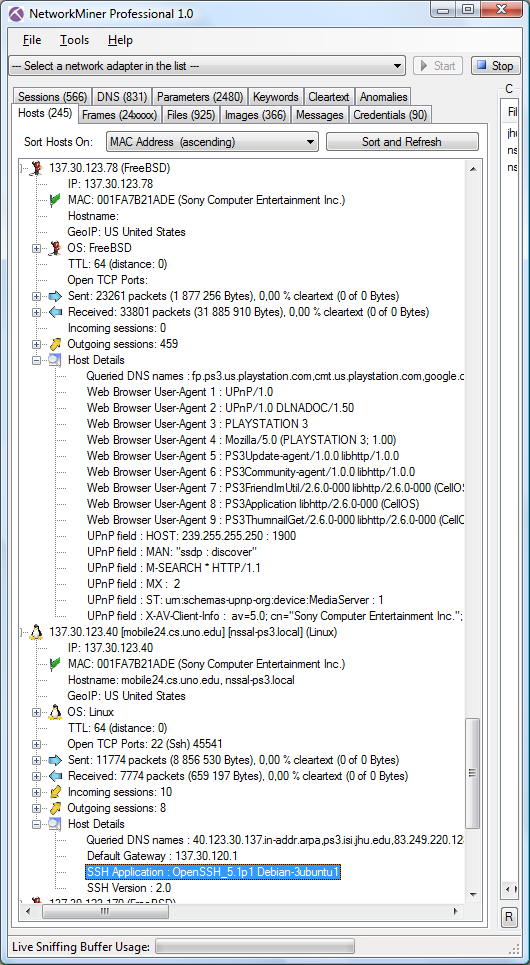
NSSAL's PS3 was later rebooted into Ubuntu Linux with IP 137.30.123.40 (notice that the MAC address in the screenshot above remained unchanged). I could tell that NSSAL's PS3 was running Ubuntu Linux since the OS fingerprinting functionality provided by Satori and p0f both show that the TCP/IP stack behaves as Linux. The SSH banner-grabbing functionality included in NetworkMiner also says that NSSAL's machine was running "OpenSSH_5.1p1 Debian-3ubuntu1".
I should probably also mention the backdoor I found being used by JHUISI to get into NSSAL's machine. The initial commands sent in the remote shell session from when this backdoor was used looks as follows:
jhuisi
Backdoor by darkXside
Enter the second password.
mac
Password accepted!
[backdoor]# ls
backd00r
Examples
[backdoor]# ls
backd00r
Examples
[backdoor]# rm backd00r
This backdoor sure looks very much like a modified version of darkXside's backd00r.c to me.
By the way, I will try to provide a similar analysis of the DFRWS challenge from 2008 on this blog sometime in the near future. The 2008 challenge was in fact much more interesting to investigate, from a network forensics perspective, than the 2009 challenge that we have looked at in this blog post.
Posted by Erik Hjelmvik on Wednesday, 26 January 2011 20:26:00 (UTC/GMT)



