Proxocket - A Winsock Proxy Sniffer
There are many ways to capture network traffic on Windows machines. The most common way is undoubtedly to use a link-layer driver such as WinPcap's NPF-driver or Microsoft's Network Monitor driver. These drivers are typically used by applications like Wireshark and Microsoft's Network Monitor to provide low level network access, so that packets can be captured without having to pass through the TCP/IP stack.
Another sniffing option is to use Raw Sockets, which can be used to capture traffic one more layer up the stack (between the Link and Internet layer). Raw Sockets is, however, a topic that I plan to cover more in detail on this blog in the future so I will not dwell any more on it in this post.
What I really wanna write about in this blog post is a third way to capture network traffic: Winsock proxy capturing.
Luigi Auriemma has built a great tool called Proxocket, which can be used to capture calls between an application and the Winsock functions in Windows. Proxocket is simply two DLL files (ws2_32.dll and wsock32.dll) which should be placed in the same directory as the .exe of the application for which you wanna monitor network traffic. These DLL files act as proxies to the real Winsock DLL files (with the same names), which reside in "C:\Windows\System32\". Placing Luigi's proxy DLLs in the same folder as the .exe file causes the application to load the proxy DLLs rather than the real Winsock DLLs. Proxocket relays all packets between the application and the real Winsock DLLs, but every relayed packet is also written to a .cap file by Proxocket.
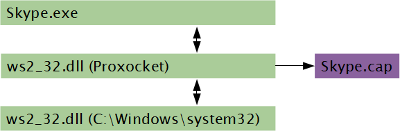
Not only does Proxocket let you sniff the traffic to and from an application without having to load a new network driver or raw socket sniffing application,
it also makes it possible to sniff traffic going to localhost.
But why would someone wanna establish a network connection to localhost, you might ask.
I have personally used localhost sockets in my applications when I have code running in different processes or threads and need an effective way for them to exchange data in an asynchronous manner (NetworkMiner does not use localhost sockets for inter-process communication though).
I'm actually pretty sure many software developers use localhost sockets when they need to provide data exchange between different processes.
Localhost connections are also used when running Stunnel or TOR proxies on your local machine,
which encrypt all outgoing traffic.
You can thereby use Proxocket in order to capture the network traffic BEFORE it is encrypted by Stunnel or TOR.
I have found Proxocket very practical when I need to capture traffic from just a single application. I did, for example, use Proxocket when collecting training data for obfuscated protocols (like BitTorrent's MSE protocol and Skype) when laying the grounds for my "Breaking and Improving Protocol Obfuscation" report.
By the way, Luigi is probably primarily known for being the number one vulnerability discoverer of all time according to X-Force in 2008 (I'm not sure he still holds the #1 spot though). He seems to have a special interest for finding and reporting bugs in computer games, and I do suspect Proxocket comes in quite handy when doing that type of vulnerability analysis.
Posted by Erik Hjelmvik on Thursday, 20 January 2011 20:05:00 (UTC/GMT)



